* 程序的加解密函数存在缺陷,可以通过明文和密文逆向还原密钥
* 后台登陆处没有有效验证cookie有效性导致攻击者可以通过伪造cookie登陆后台
* 后台可以上传shell
下面一步一步来看
首先是加解密函数eccode
可以看到密文是明文与key通过字符ascii相加最后base64编码后得到的,加密时,key由最后一位开始,依次与明文的每一位进行ascii相加,因此用密文和明文相减能得到key,有没有凯撒加密的感觉?
知道原理以后下面开始逆向key:
好吧,虽然现在理论上可以还原key了,但是还得找到足够长的明文和相对应的密文才可以得到完整的key,毕竟如果明文和密文都没有key长,还原得到的key也是不完整的。
在购物车结算时,程序会把当前物品的价格和折扣变成md5然后加密后放到cookie里,所以我们可以保证推算出最多32位长的key,够了,至于其他的地方不知道可不可以,我没有仔细看。
而被加密的明文就是MD5过后的购物价格,因此可以还原最长32位的key
在经过上面的步骤还原key以后,就可以伪造cookie登陆后台了:
需要cookie中的将esp_powerlist设为all,将ecisp_admininfo设为类似'1|hym|12345678901234567890123456789012|'.md5('Mozilla/5.0 (Windows NT 6.1; WOW64; rv:18.0) Gecko/20100101 Firefox/18.0').'|1|management|'.md5('http://**.**.**.**/espcms/adminsoft'这样的结构,去登陆后台就可以了,此处应有掌声。
首先注册会员购物
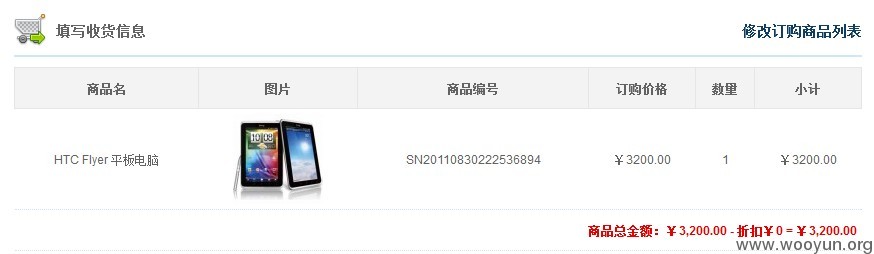
折扣前和折扣后的价格都是3200,所以明文是
md5('3200|3200')='38a7a5650e6296b180c88f6592486fbf'
密文通过查看cookie中的ecisp_order_sncode得到:
ecisp_order_sncode=mHGWbpJsapiRnZhjbG6WlWtnlpxqzG6XbWlsa5ufl50
写了一个poc来还原key:
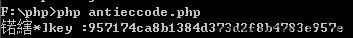
通过检查,发现后面实际是重复的,因此真正的key应该是前面的957174ca8b1384d373d2f8b4783e
key正是"957174ca8b1384d373d2f8b4783e"
然后设置cookie并登陆,浏览器要与poc中设置的浏览器一致,否则会登陆失败
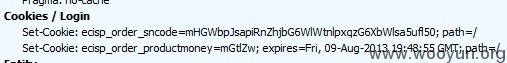
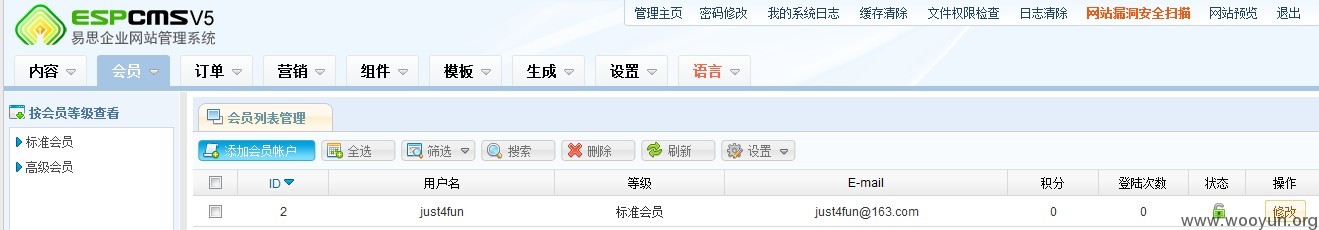
进入后台后getshell的方法有很多,就不说了。






