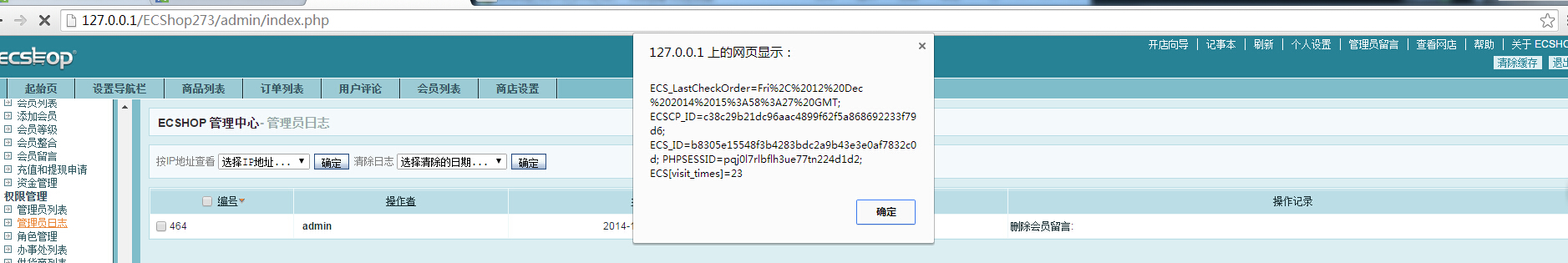
N久了,你们是修还是不修啊?这么蛋疼的一个漏洞.
先看admin_logs.php代码
没有做任何过滤转义
但是管理员日志正常用户是没有办法直接控制的,我们就需要想办法间接去控制他
继续翻找代码 找关键字admin_log 找到有哪写代码会往日志数据库写数据的
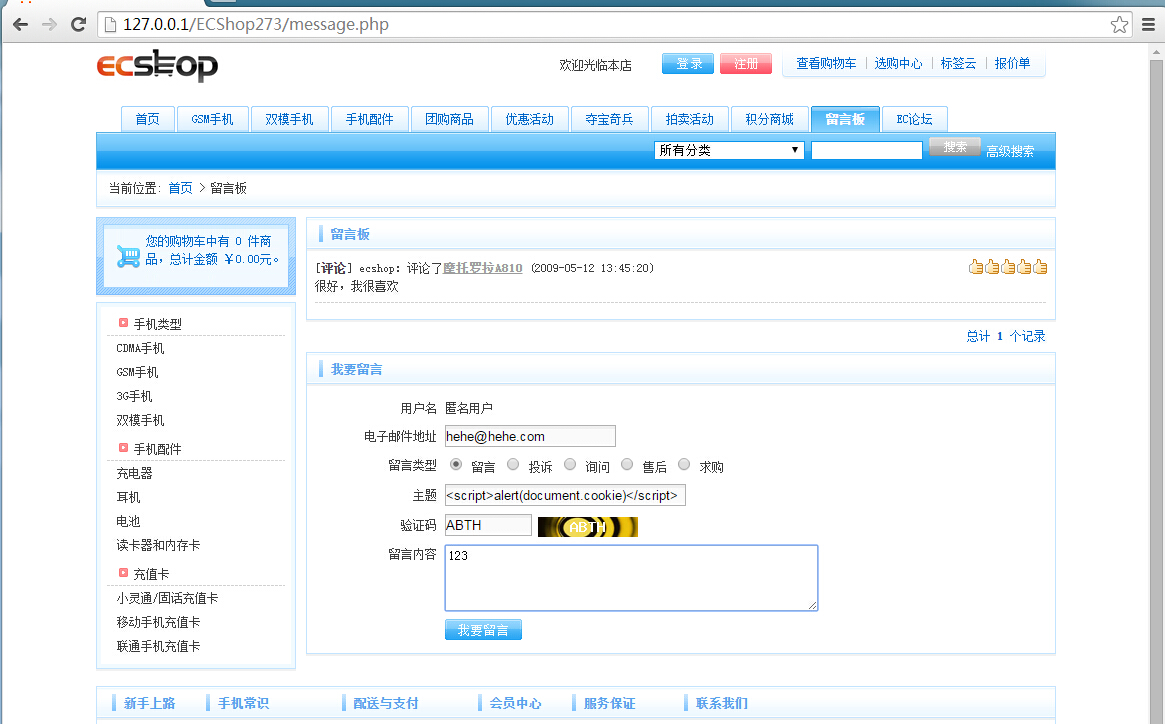
找到user_msg.php文件有处 而这个是用来审核用户留言的 也就是说可控
发现这里直接把 $msg_title写进了admin_log
$msg_title 是留言的标题 那在找留言出代码
也没有对代码进行过滤 msg_title也是直接写入