官方提供了老版本的源码下载 分析代码发现适用于最新版的漏洞
存在的5处注入均处于登录位置
/System/目录下源码无法解密出来 以/Android/Login.php 为例
114-120行:
iconv函数引发的宽字节注入
由于enableq登录要获取一个特定随机值 而且 对ip做了限制(可通过XFF绕过)
所以写了python脚本获取用户数据
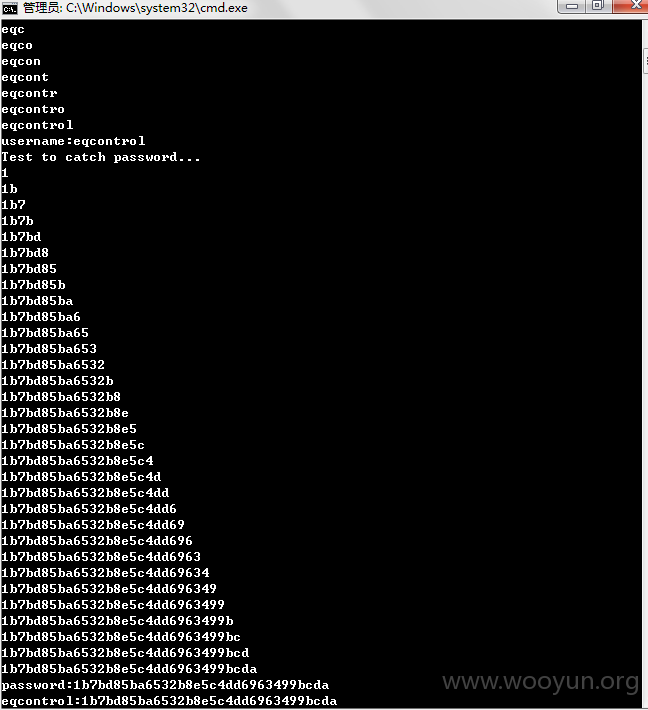
获取demo管理员数据 登录
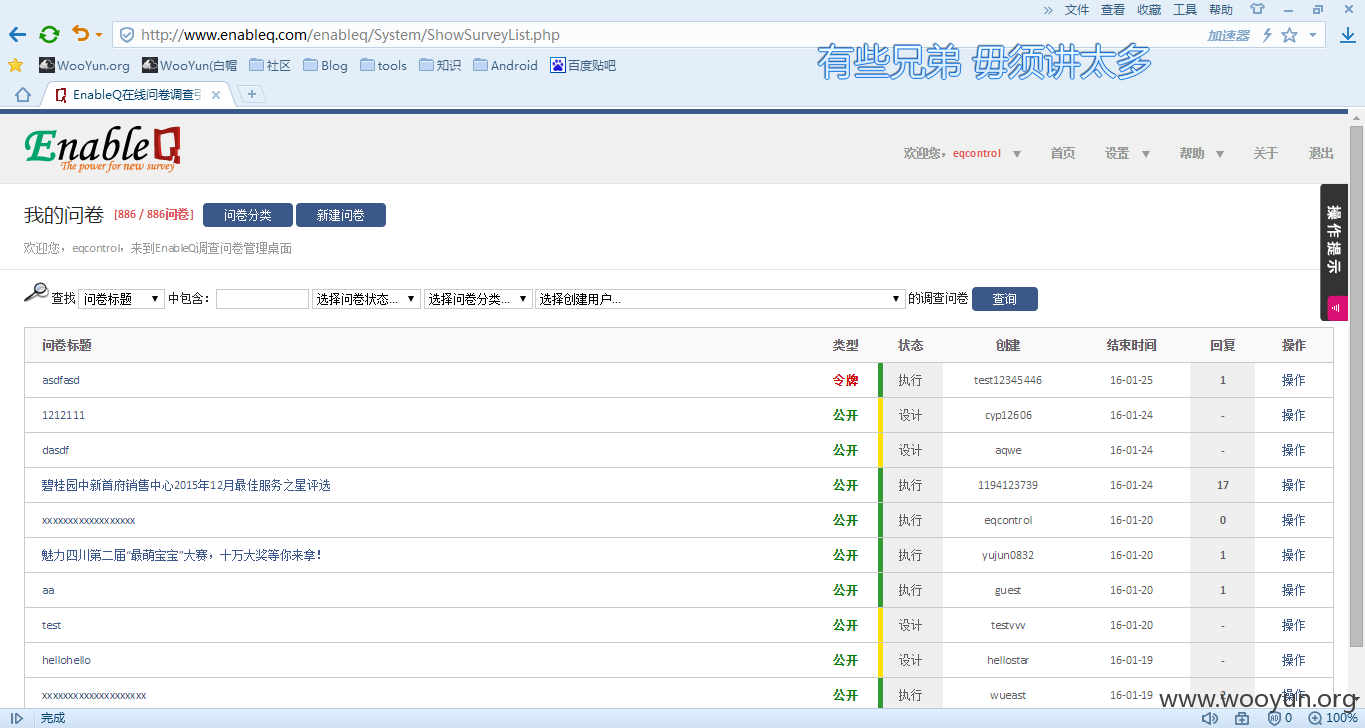
接下来就是后台getshell部分
/License/License.php
这段代码就是把上传的xml文件copy到License/License.xml
再看
包含进去 导致Getshell 而这个文件会调用到每个文件 于是连接首页也行

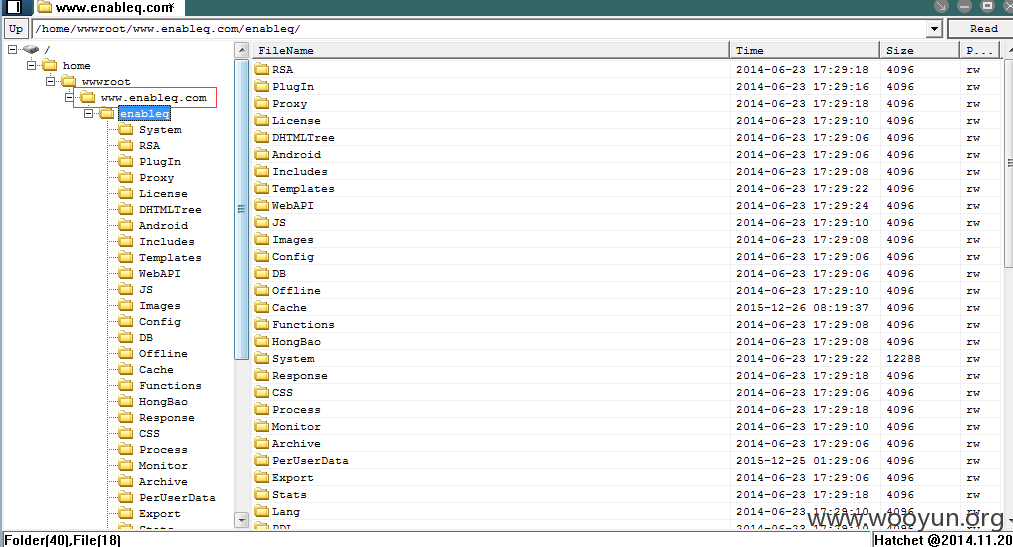
主站沦陷
官方提供了老版本的源码下载 分析代码发现适用于最新版的漏洞
存在的5处注入均处于登录位置
/System/目录下源码无法解密出来 以/Android/Login.php 为例
114-120行:
iconv函数引发的宽字节注入
由于enableq登录要获取一个特定随机值 而且 对ip做了限制(可通过XFF绕过)
所以写了python脚本获取用户数据

获取demo管理员数据 登录

接下来就是后台getshell部分
/License/License.php
这段代码就是把上传的xml文件copy到License/License.xml
再看
包含进去 导致Getshell 而这个文件会调用到每个文件 于是连接首页也行


主站沦陷