这里一共存在九处SQL注入及越权操作!!!
文件/member/model/com.class.php
第一处SQL注入、越权删除职位信息:
这里的$delid=$_GET['del'];
没有经过任何保护直接进入:DB_delete_all和DB_select_all
跟进DB_delete_all函数:
这里也没有处理,导致SQL注入
而且这里可以通过截断后面的:and `uid`='".$this->uid."'",修改uid的值,uid为用户的用户id,这样就可以越权操作,删除任意用户的职位信息了。
第二处SQL注入、越权删除用户系统信息:
这里的$ids=$_GET['del'];
没有经过任何保护进入了DB_delete_all函数,导致SQL注入
由于这里的fa_uid就是此用户的uder id,这里我们通过截断后面的fa_uid,修改fa_uid为任意用户的id,就可以通过越权操作,删除任意用户的系统信息了。
第三、四、五、六处SQL注入、越权操作:
上面的注入点都已经表名,见后面的漏洞证明,证明漏洞存在
第七处SQL注入、越权删除黑名单
这里的$id=@implode(",",$_POST['delid']);
没有经过保护直接进入了DB_delete_all,导致SQL注入,通过截断,修改uid可以删除任意用户的黑名单信息。
第八处SQL注入、越权删除用户邀请信息
这里的$id=$_GET['del'];
没有经过保护直接进入了DB_delete_all,导致SQL注入,通过截断,修改uid可以删除任意用户的邀请信息。
第九处SQL注入、越权操作
这里的$id=$_GET['del']?$_GET['del']:@implode(",",$_POST['delid']);
没有经过保护直接进入了DB_delete_all,导致SQL注入,通过截断,修改uid可以删除任意用户信息。
这里拿第一处SQL注入、越权删除职位信息为例:
两个企业用户:
攻击者:111111,uid=3,发布的职位信息id=2,
受害者:222222,uid=4,发布的职位信息id=4,
我们先来看看用户222222发布的职位信息:
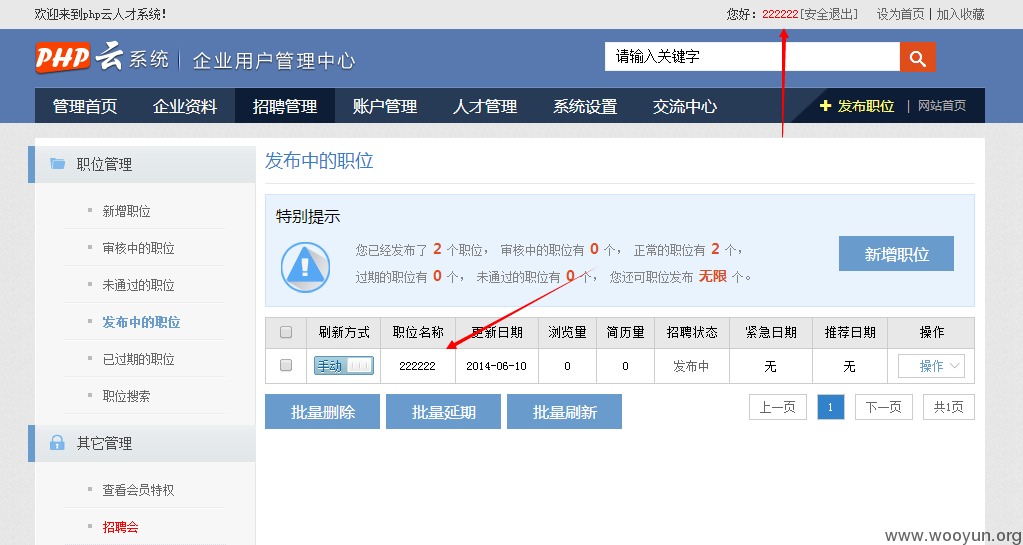
然后用户111111发送请求:
http://localhost/phpyun/member/index.php?c=job&del=if(substring(user(),1,1)=char(111),4,888))/**/and `uid`=4%23
将uid设置为受害者222222的uid=4
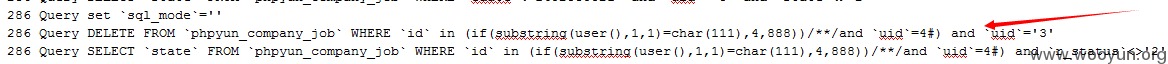
这然后查看用户222222的发布职位信息,仍然存在,没有删除
修改char的值,继续发送请求:
http://localhost/phpyun/member/index.php?c=job&del=if(substring(user(),1,1)=char(114),4,888))/**/and `uid`=4%23
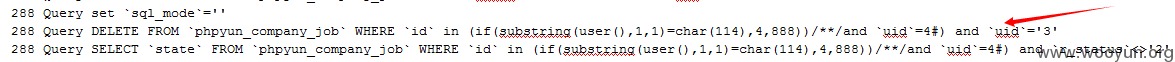
此时在访问用户222222的发布职位信息时,职位信息已经被删除:
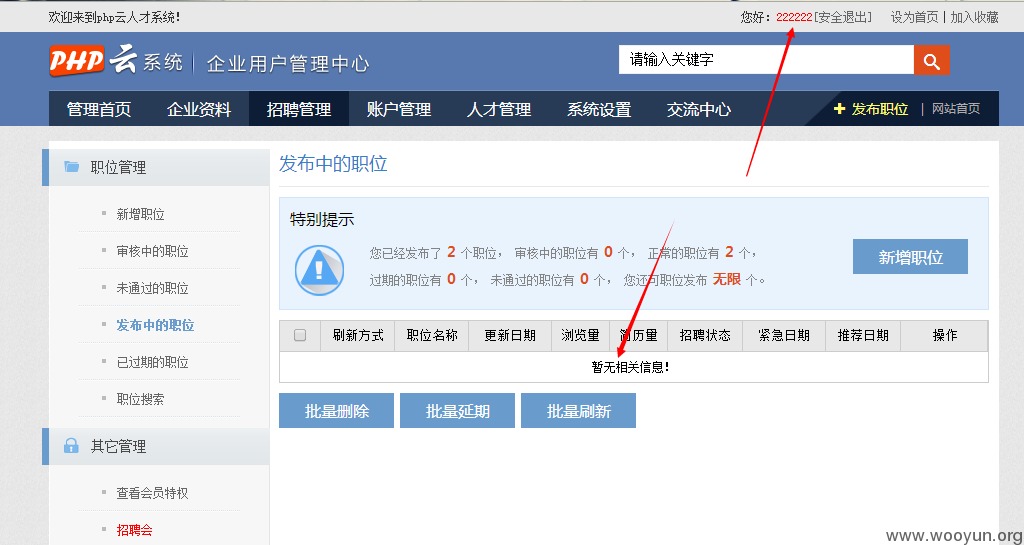
这列通过修改char的值,遍历得到user()=root
也通过设置uid为其他任意用户,导致越权操作,可删除其他用户的发布职位信息。







