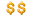U-Mail最新版V9.8.59
环境:win2003+官网下载最新版(官网下载显示v9.8.57版本,其程序最后更新时间为2015.03.26修正了很多漏洞,安装后在web目录查看version.txt发现实际版本是v9.8.59)
如图
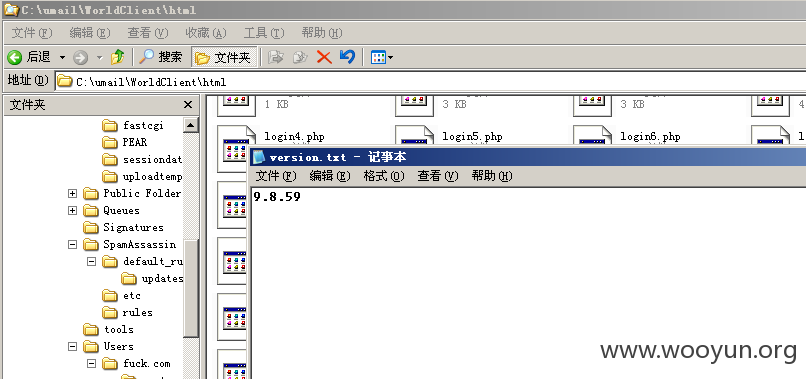
漏洞修复不当,导致sql注入,可获取管理员密码。
旧版漏洞分析http://**.**.**.**/bugs/wooyun-2015-093376,新版更新了,修复了多个sql注入,其中修复该二次注入时候,其在更新资料处做了过滤函数,旧版的入库文件为
/client/option/module/o_userinfo.php
代码为

查看过滤函数
/admin/include/base.func.php代码为
其过滤了mysql的注释符,很明显这种方式不妥,这种类似黑名单的修复方式很容易被绕过,这里使用mysql的--注释符即可绕过,注意注释符--后要跟个空格。
而该漏洞文件/client/oabshare/module/operates.php内容仍然未变化,其应该在该文件的数据出处加过滤
漏洞利用:
登录邮箱后,点击更新个人资料,
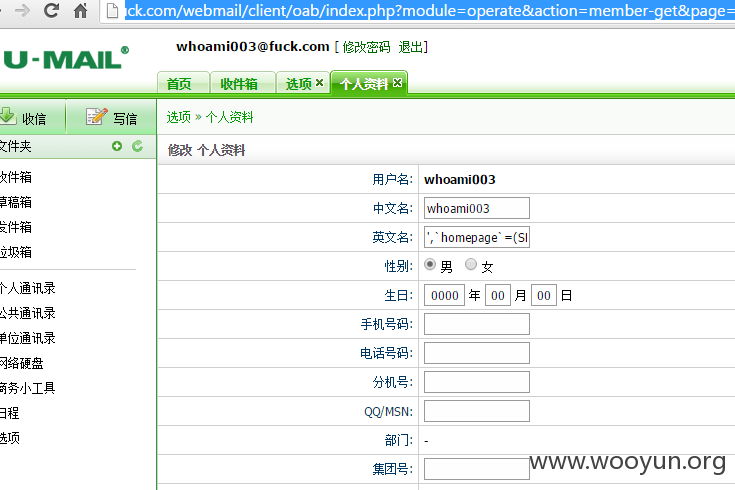
请求为
更新个人资料的sql语句
更新资料后获取用户的userid,执行请求为
http://**.**.**.**/webmail/client/oab/index.php?module=operate&action=member-get&page=1&orderby=&is_reverse=1&keyword=whoami003
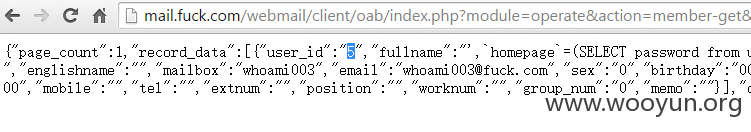
其执行的其执行的入库sql语句为
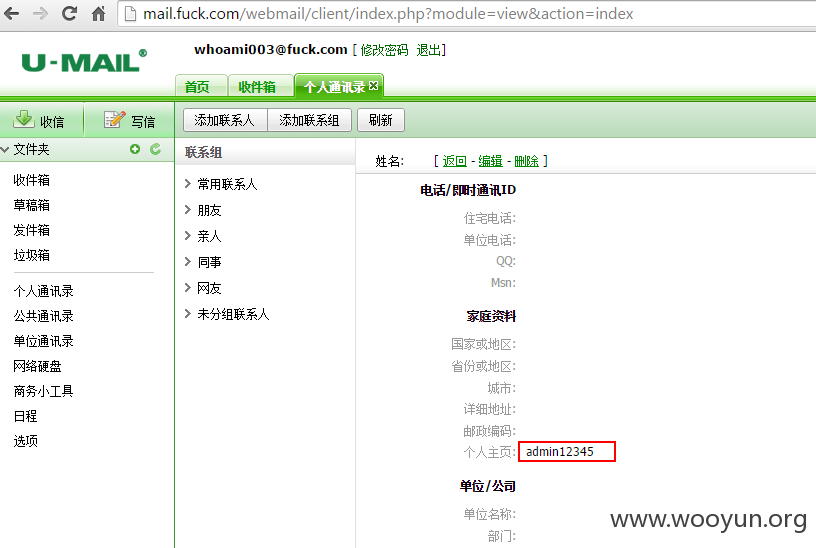
在个人通讯录中查看管理员密码
二、注入2
原理类似,该文件/client/oab/module/operates.php也存在注入,之前的分析http://**.**.**.**/bugs/wooyun-2010-099221